Premium Only Content
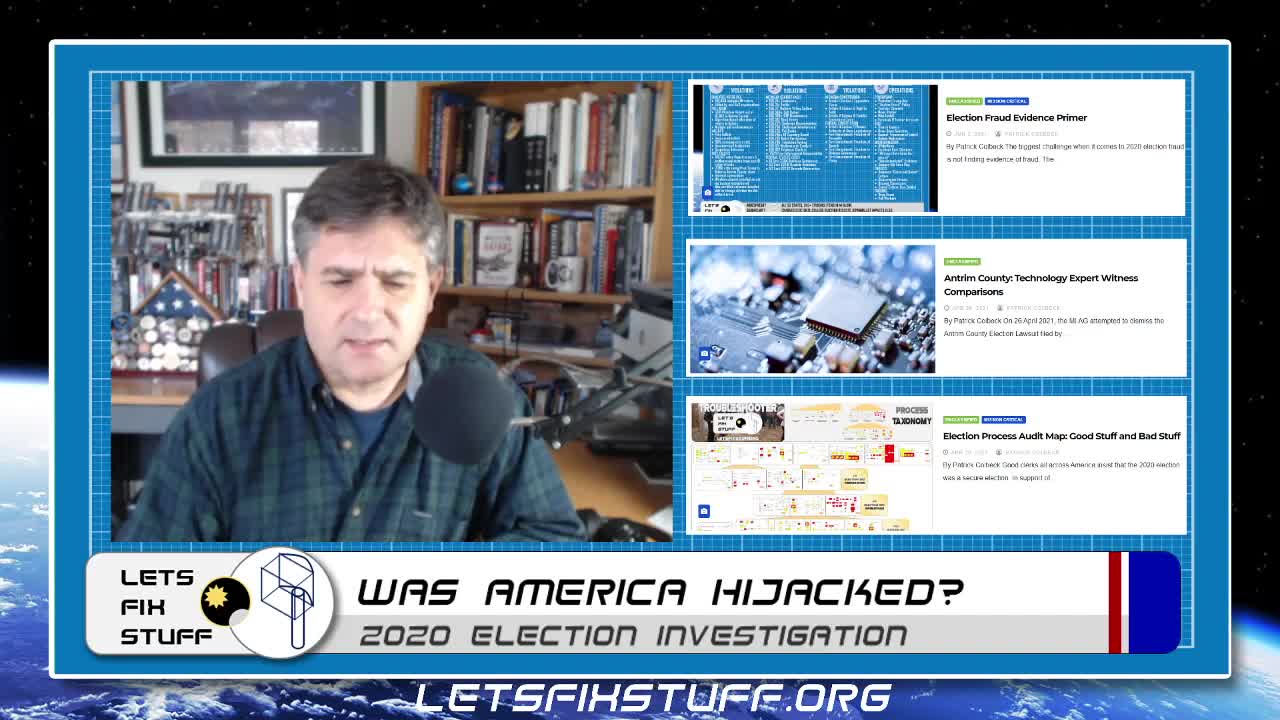
How the 2020 Election Was Stolen
Former Michigan Senator Patrick Colbeck gives an excellent breakdown of the 2020 election robbery from a systems engineering perspective.
Colbeck partitions the steal into 4 phases:
1) Preparation
The key goal of this phase is to create and exploit weaknesses in our election system. How? By weakening the election record chain of custody for the (i) qualified voter file (QVF), (ii) poll books, (iii) ballots, and (iv) vote tally.
The criminals start by seeding the QVF. For example, there were more than 616K ineligible voters in the Michigan QVF heading into the 2020 election.
Other weakening measures include no-excuse absentee voting, same-day voter registration, elimination of voter ID and signature verification requirements, and centralized, networked, voting systems. All of these erosions reduce the number of bad actors needed to steal an election.
2) Main Attack
The central tool in this second phase is ballot stuffing via mail-in votes, enabled by seeding the QVF with low propensity and ineligible voters.
Importantly, phase 2 requires an accurate prediction of voter turnout to be successful. If those forecasts fail (as they did in the 2020 election), the perpetrators have to shift to a backup plan, the Backup Attack phase.
3) Backup Attack
Phase 3 involves algorithmic manipulation of the vote tally when ballot stuffing isn’t netting enough votes.
Lady Draza identified a digital fingerprint for something called the “PID controller” during this phase. As she was monitoring the election night results in multiple states, she noticed the cumulative vote total would periodically drop to zero in the Edison reporting stream before surging back up. This is NOT normal.
Once the vote tallies have been altered, ballots must be added for reconciliation. And, that’s exactly what we saw with the 3AM ballot drop-offs at the TCF center and the halted late-night vote counts in every swing state.
4) Defense
The defense phase involves censorship and evidence destruction.
Colbeck says canvassing is critical to combat the fraud, and recommends starting with the QVF.
Also on Colbeck’s investigation wishlist: an audit of the election night reporting results, from the precinct level to the New York Times. No one has done this yet.
-
 55:07
55:07
LFA TV
1 day agoDefending the Indefensible | TRUMPET DAILY 2.25.25 7PM
33.7K14 -
 6:09:26
6:09:26
Barry Cunningham
12 hours agoTRUMP DAILY BRIEFING - WATCH WHITE HOUSE PRESS CONFERENCE LIVE! EXECUTIVE ORDERS AND MORE!
86K50 -
 1:46:37
1:46:37
Game On!
7 hours ago $0.51 earnedPUMP THE BRAKES! Checking Today's Sports Betting Lines!
51.6K3 -
 1:27:21
1:27:21
Redacted News
7 hours agoBREAKING! SOMETHING BIG IS HAPPENING AT THE CIA AND FBI RIGHT NOW, AS KASH PATEL CLEANS HOUSE
198K245 -
 1:08:28
1:08:28
In The Litter Box w/ Jewels & Catturd
1 day agoCrenshaw Threatens Tucker | In the Litter Box w/ Jewels & Catturd – Ep. 749 – 2/25/2025
116K56 -
 44:57
44:57
Standpoint with Gabe Groisman
1 day agoWill Byron Donalds Run for Florida Governor? With Congressman Byron Donalds
60.8K9 -
 1:06:25
1:06:25
Savanah Hernandez
6 hours agoEXPOSED: FBI destroys evidence as NSA’s LGBTQ sex chats get leaked?!
81.9K30 -
 1:59:58
1:59:58
Revenge of the Cis
8 hours agoEpisode 1452: Hindsight
68.7K11 -
 1:20:35
1:20:35
Awaken With JP
10 hours agoCrenshaw Threatens to Kill Tucker and Other Wild Happenings - LIES Ep 80
133K74 -
 1:32:19
1:32:19
Russell Brand
9 hours agoBREAK BREAD EP. 15 - LECRAE
138K10