Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.

Different Types of X-Hat Hackers : Simply Explained!
4 years ago
80
dark web deacon
dark web
dark net
dark web movie
cyber security
hacker
hacking
what are black hat hackers
what are black hats
what are white hat hackers
what are grey hat hackers
In this episode we will go over the 6 types of X-Hat hackers: black hat, white hat, grey hat, green hat, blue hat, and red hat hackers along with script kitties.
Enjoy: Different Types of X-Hat Hackers : Simply Explained!
#DarkWebDeacon #TypesofHackers #BlackHat #WhiteHat #GreyHat #GreenHat #BlueHat #RedHat
Loading comments...
-
 6:51
6:51
Dark Web Deacon
2 years agoDark Web Assassins - Beyond Surreal Series DWD Cut
3.14K1 -
 6:21
6:21
CookFilms
4 years agoDifferent lens filters explained for videography
11 -
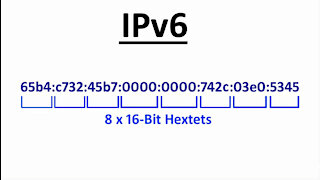 9:43
9:43
Ace Networker
4 years agoIPv6 Explained Simply - The Basics of IPv6
1291 -
 1:15
1:15
NowYouKnowEnglish
4 years agoWhat Are The Different Types Of Rests ? *
334 -
 1:15
1:15
NowYouKnowEnglish
4 years agoWhat Are The Different Types Of Rests ?
1.88K -
 4:12
4:12
Dark Web Deacon
4 years agoWhat Is Social Angler Phishing? : Simply Explained!
225 -
 5:07
5:07
NCJFILMS
4 years ago $0.12 earnedDifferent types of gamers
327 -
 4:46
4:46
Meteorology101
4 years agoCloud Dynamics & The Different Fog Types
13 -
 13:24
13:24
Exploring With Nug
11 hours ago $2.15 earnedSearching For Missing Woman Using Underwater Drone!
22.1K1 -
 LIVE
LIVE
2 MIKES LIVE
4 hours ago2 MIKES LIVE #206 News Breakdown Wednesday!
189 watching