Premium Only Content
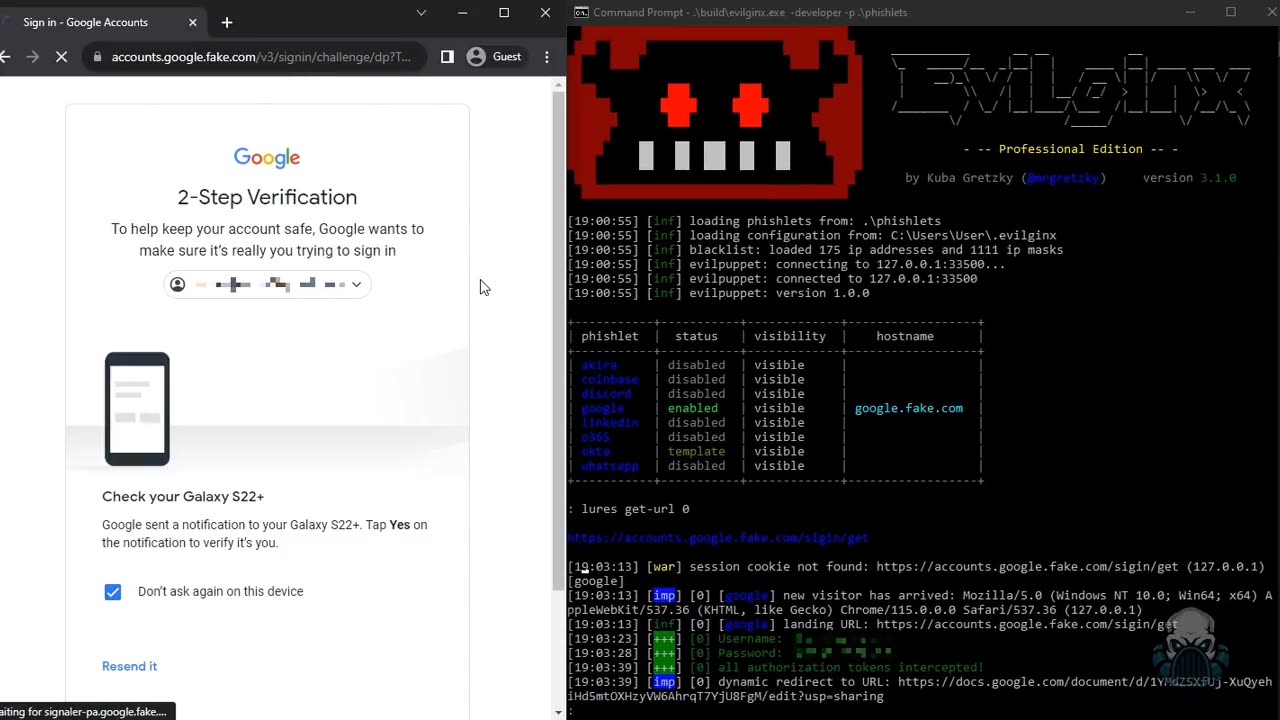
Bypassing two step verification using session tokens via reverse proxy phishing 🌐
Reminder Hacking into networks or systems that you don't own without permission is illegal. This was performed on my own equipment
🔒 Evilginx: The Cyber Phantom 👻
Evilginx, a notorious phishing tool, made waves in the cybersecurity world when it first emerged, targeting unsuspecting users through advanced "man-in-the-middle" attacks. Initially developed for Linux, it quickly gained notoriety for its ability to bypass two-factor authentication (2FA), a feature meant to be a safety net against cyberattacks.
By acting as an intermediary between the victim and legitimate websites, Evilginx captures sensitive information like usernames, passwords, and even 2FA tokens, all without triggering suspicion. Cybercriminals use it to impersonate popular platforms like Google, Facebook, and Instagram, making it a nightmare for both users and security experts.
Evilginx shows how sophisticated cyberattacks have become – and why we must always stay vigilant online. 💻🔐
#Cybersecurity #Phishing #Evilginx #Linux #Hackers #StaySafe #2FA #OnlineSecurity
Follow the creator of the tool on Twitter/X
@mrgretzky
EDUCATIONAL PURPOSES ONLY!!!
-
 1:43:21
1:43:21
Redacted News
8 hours agoBREAKING! UKRAINE AGREES TO CEASEFIRE WITH RUSSIA... BUT THERE'S A BIG CATCH | Redacted News
172K302 -
 58:17
58:17
Candace Show Podcast
8 hours agoShould We Feel Bad For Blake Lively? | Candace Ep 157
139K273 -
 3:06:52
3:06:52
The Nerd Realm
9 hours ago $11.46 earnedHollow Knight Voidheart Edition #19 | Nerd Realm Playthrough
84.4K6 -
 1:17:27
1:17:27
Awaken With JP
11 hours agoThe Current Thing: Tesla Protesting - LIES Ep 82
146K70 -
 1:07:08
1:07:08
Sean Unpaved
8 hours agoNFL Free Agency Rolls On! MLB Spring Training Heats Up along with 3x World Series Champ Dave Stewart
87.6K3 -
 2:10:15
2:10:15
Right Side Broadcasting Network
13 hours agoLIVE REPLAY: White House Press Secretary Karoline Leavitt Holds Press Briefing - 3/11/25
174K43 -
 2:06:00
2:06:00
The Quartering
12 hours agoTrump Goes NUCLEAR On Canada, Blasts Massie, Harry Potter Race Swap, Man Humiliated On TV Show
125K67 -
 1:03:09
1:03:09
The White House
11 hours agoPress Secretary Karoline Leavitt Briefs Members of the Media, Mar. 11, 2025
119K72 -
 1:07:03
1:07:03
Winston Marshall
11 hours agoEXCLUSIVE : Oliver Anthony On Life After ‘Rich Men’, The Christian Counter Culture and The Elites
79.2K12 -
 1:44:47
1:44:47
Russell Brand
12 hours agoDigital Censorship & Political Warfare: X Attacked, Rand Paul Rebels, Free Speech on Trial – SF551
174K28