Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
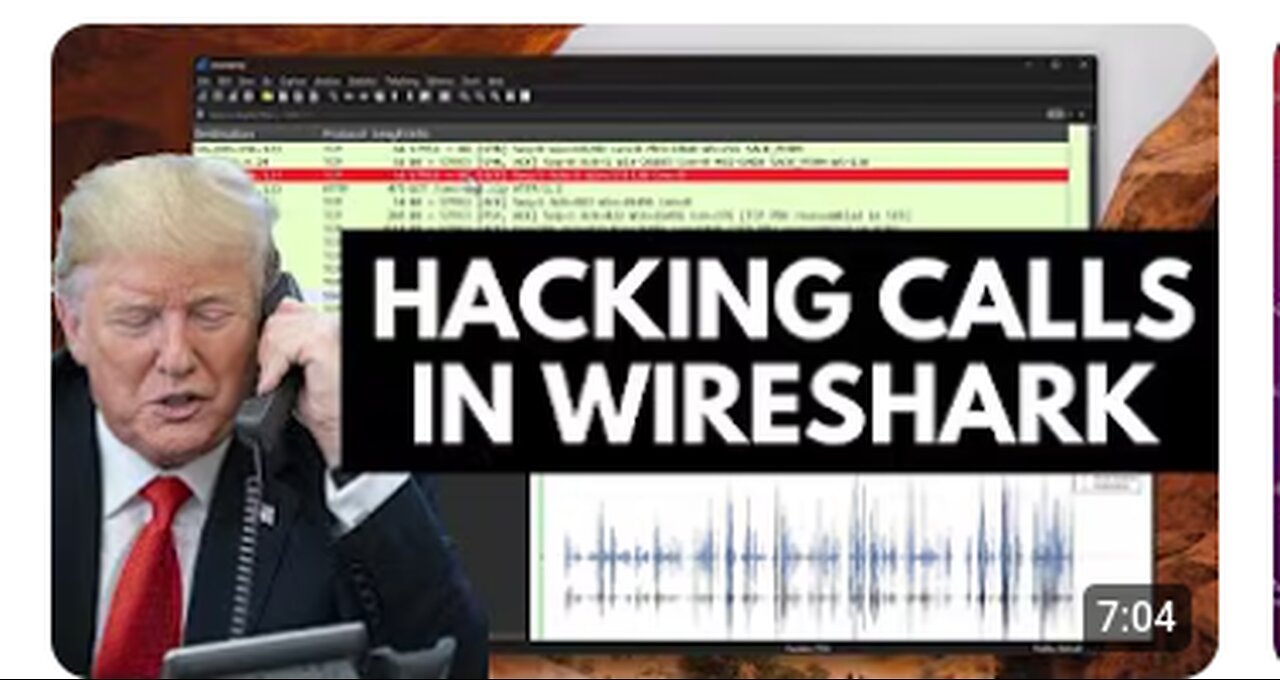
How calls can be hacked: Wireshark Forensics 101
2 months ago
87
How calls can be hacked: Wireshark Forensics 101
https://www.youtube.com/watch?v=kzJqdgyGsHw
Loading comments...
-
 LIVE
LIVE
Focus_Up
1 hour agoGrandpa out playing kids on Warzone!! Playing with subscribers!! come say hi!!
112 watching -
 LIVE
LIVE
PizzaSlayer
6 hours ago🍕🗡️{Switched to Siege} Hawaii so Kawaii ^_^🍕🗡️
212 watching -
 LIVE
LIVE
Dabkillah
6 hours ago🔴LIVE-DABKILLAH-FORTNITE-KICKASS AND TAKING NAMES
86 watching -
 LIVE
LIVE
Joker Effect
59 minutes agoRAGE?! How about Gaming on RUMBLE?! Tonight...The Real Joker rages at The First Berserker
346 watching -
 LIVE
LIVE
Vorrhese
1 hour agoLIVE: The First Berserker: Khazan - Lets Play!
166 watching -
 LIVE
LIVE
rosssims
1 hour agoSims Games: Simsy plays Stardew Valley ‽ ‽ ‽
55 watching -
 10:09
10:09
China Uncensored
7 hours agoTrump Just Hit China Where It Hurts
6.22K5 -
 2:42:25
2:42:25
DrDamon
3 hours ago🟢 LIVE - Old Man Gets Carried in Video Games | USE CODE: "DRDAMON"
7.15K -
 LIVE
LIVE
Koke
5 hours agoCore Keeper Bags & Blasts Hardcore - Bird Boss!
56 watching -
 44:15
44:15
Film Threat
7 hours agoLIVE FROM WONDERCON IN ANAHEIM | Film Threat Live
8.7K