Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
2. Scams and external threats (part 1)
1 month ago
17
Finance
SeguridadDigital
Ciberamenazas
EstafasOnline
Ciberseguridad
ProtegeTuDatos
AmenazasExternas
CuidadoConElFraude
DefensaCibernética
PrevenciónDeEstafas
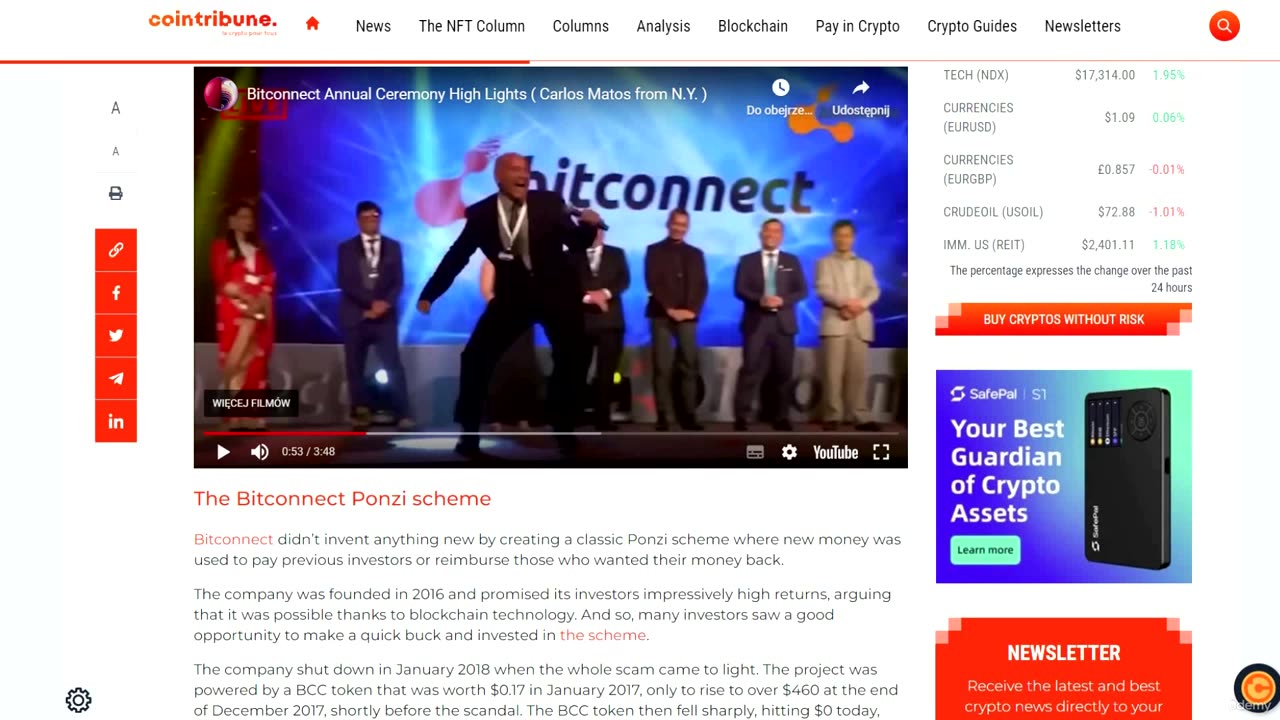
2. Scams and external threats (part 1)
Loading 1 comment...
-
 1:19:48
1:19:48
The Rubin Report
5 hours agoWhat the Trump Administration Must Do Instead of Revenge | Peter Thiel
55K76 -
 1:59:00
1:59:00
Steve-O's Wild Ride! Podcast
3 days ago $31.66 earnedPatrick Bet-David DESTROYS Steve-O's Dad - Wild Ride #252
99.7K37 -
![[XboxONE] GRINDING 1000g FC24](https://1a-1791.com/video/fwe1/01/s8/1/y/k/I/o/ykIoy.0kob-small-XboxONE-GRINDING-1000g-FC24.jpg) 3:29:15
3:29:15
deathbee
9 hours ago[XboxONE] GRINDING 1000g FC24
57.4K2 -
 1:08:32
1:08:32
Winston Marshall
1 day agoThe HIDDEN Agenda: Congresswoman Hageman UNCOVERS USAID Fraud, Censorship and Human Trafficking
90.5K118 -
 8:16
8:16
CarlCrusher
22 hours agoThe True Story of Stranger Things and the Montauk Project Origins
42.6K11 -
 10:05
10:05
ariellescarcella
23 hours agoNo, You're Not Having A 'Gender Crisis' You're Just Bored
52.6K33 -
 41:08
41:08
The Finance Hub
1 day ago $11.98 earnedBREAKING: DONALD TRUMP JR. SHOCKS THE WORLD!
44.8K92 -
 8:04
8:04
BIG NEM
1 day agoHow Your Mind SHAPES Reality! 🧠 Epigenetics, Psychedelics & Quantum Physics Explained!
50.8K5 -
 33:44
33:44
hickok45
11 hours agoSunday Shoot-a-Round # 270
39.3K20 -
 32:24
32:24
Degenerate Plays
1 day ago $1.17 earnedThe Floating Cuck Chair?! - Sonic The Hedgehog (Sonic Origins) : Part 1
34.5K2