Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
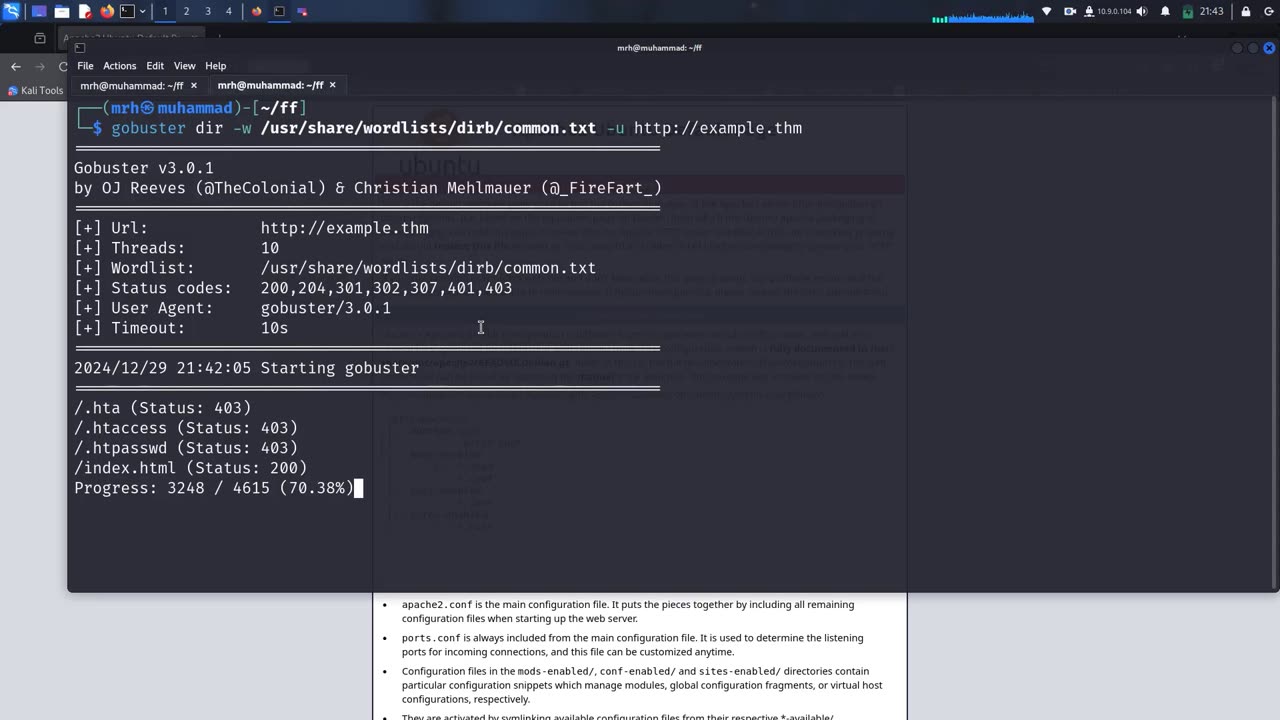
How Hackers Exploit Websites in Minutes: A Security Guide
1 month ago
5
HowTo
Evil West
how hackers hack websites
website hacking techniques
cybersecurity tutorial
protect your website
ethical hacking guide
website vulnerabilities
how hackers breach websites
web security tips
website hacking in minutes
How Hackers Exploit Websites in Minutes: A Security Guide
Loading comments...
-
 2:05:26
2:05:26
TimcastIRL
10 hours agoTrump NUKES IRS, Mass Fed Layoffs, Democrats REVOLT Over 200k Layoffs w/Roma Nation | Timcast IRL
127K175 -
 1:39:03
1:39:03
Roseanne Barr
14 hours ago $29.99 earnedAdam Carolla! | The Roseanne Barr Podcast #87
115K26 -
 1:29:04
1:29:04
Glenn Greenwald
13 hours agoTrump, Vance & Musk Announce a Radically New Foreign Policy Framework; Prof. Norman Finkelstein on Gaza's Future, the Cease-Fire Deal & Fallout from the U.S./Israeli War | SYSTEM UPDATE #407
151K96 -
 4:15:00
4:15:00
Nerdrotic
15 hours ago $49.21 earnedCaptain Falcon America REVIEW, Disney Ending DEI? Rings of Power RETURNS | Friday Night Tights #341
214K36 -
 9:34:03
9:34:03
FusedAegisTV
23 hours agoMario Galaxy, Batman, Real Talk/Politics, & MORE - V-Day 💗 Friday Variety Stream!
60.2K1 -
 1:10:49
1:10:49
Vigilant News Network
11 hours agoRFK Jr. Drops a Stunning Announcement | The Daily Dose
79.9K42 -
 49:49
49:49
Candace Show Podcast
14 hours agoEXCLUSIVE: Blake & Ryan’s Desperate Legal Strategy Exposed! | Candace Ep 147
193K135 -
 1:32:20
1:32:20
2 MIKES LIVE
12 hours ago2 MIKES LIVE #180 with guest Kyle Rittenhouse!
54.8K4 -
 9:40
9:40
Tactical Advisor
17 hours agoBest Home Defense Shotgun Build | Genesis Gen 12
48.7K4 -
 56:44
56:44
VSiNLive
14 hours ago $4.38 earnedFollow the Money with Mitch Moss & Pauly Howard | Hour 1
73.2K1