Premium Only Content
Snort Bootcamps 100% Practical For Cybersecurity Pros | Part 3
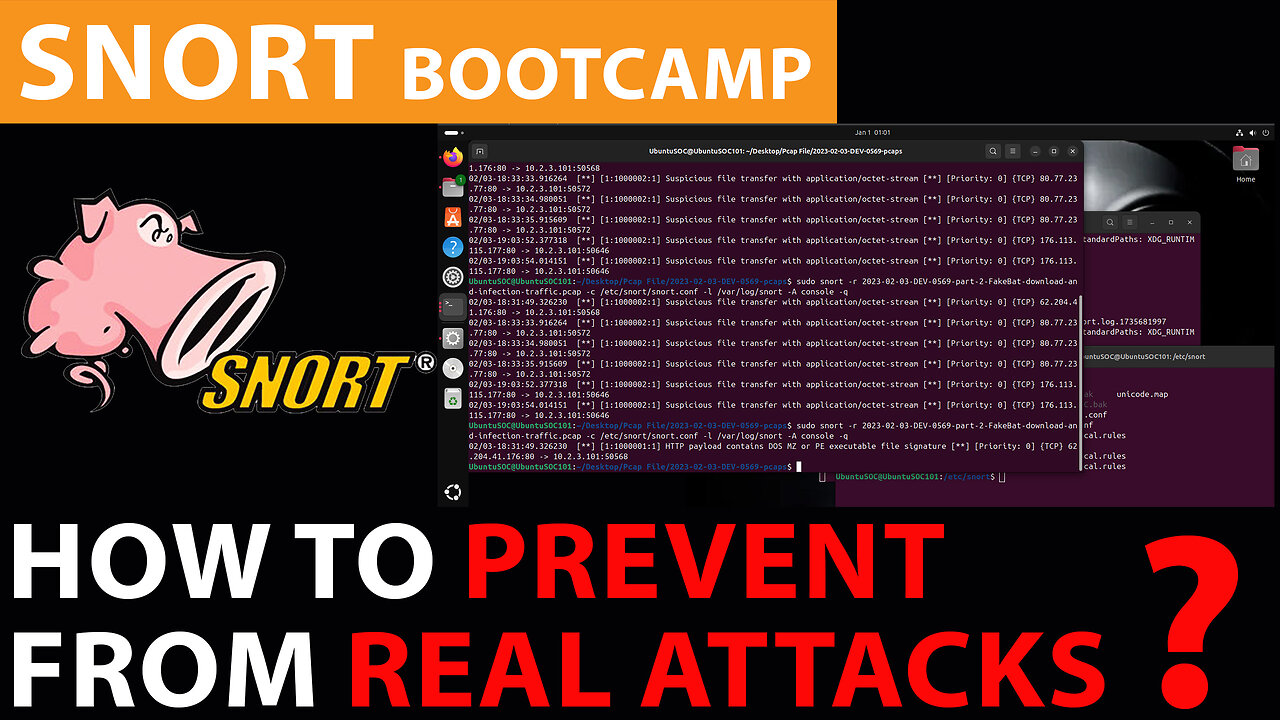
Welcome to the final and most advanced part of our Snort series! In this video, we’ll take a deep dive into writing Snort rules to defend against real-world attacks, like the fake CPU-Z malware incident. You’ll learn how to detect threats in HTTP URIs, HTTP Headers, and even the Content or Payload—covering all the key areas SOC analysts need to master. Don’t forget to like, subscribe, and follow me on YouTube and Instagram for more cybersecurity tips. Share your thoughts in the comments, and let’s level up your skills together!
My Instagram for short cyber techs and tips: https://www.instagram.com/cyberawali/
#Cybersecurity #SOCAnalyst #Snort #IDS #IPS #NetworkSecurity #MalwareDetection #FakeCPUZ #CyberDefense #SnortRules #HTTP #PayloadAnalysis #CyberThreats #SOCTraining #AdvancedSnort #CyberTips #InfoSec #CyberSecSkills #IncidentResponse #threatdetection
-
 5:49:46
5:49:46
Bitfinex
6 hours agoBitfinex Talks Live at PlanB El Salvador - Day 2
4.54K1 -
 41:47
41:47
Candace Show Podcast
3 hours agoBecoming Brigitte: An Introduction
74.6K87 -
 1:27:41
1:27:41
vivafrei
4 hours agoBernie Gets DESTROYED! Confirmation Hearings RECAP! D.C. Aviation Disaster & MORE!
69.9K56 -
 13:16
13:16
ariellescarcella
3 hours agoThese TikTok 'Trans Women' Converting To Islam Are A Problem...
2.31K5 -
![Special guest: Sam Anthony, CEO & Founder, [your] News](https://1a-1791.com/video/fwe2/e2/s8/1/B/m/X/b/BmXbx.0kob-small-Special-guest-Sam-Anthony-C.jpg) 55:09
55:09
Purham & Associates Show
4 days agoSpecial guest: Sam Anthony, CEO & Founder, [your] News
1.99K -
 1:34:42
1:34:42
The Quartering
5 hours agoNew Crash Footage PROVES Whose At Fault, Air Traffic Control Exposed, RFK Blasted, AI Issues
134K41 -
 4:56:18
4:56:18
Right Side Broadcasting Network
1 day agoLIVE REPLAY: White House Press Secretary Karoline Leavitt Holds Press Briefing - 1/31/25
280K86 -
 1:53:55
1:53:55
Twins Pod
17 hours agoThe Q Anon Shaman EXPOSES The Truth of J6! | Twins Pod - Episode 50 - The Q Shaman
73.8K16 -
 1:02:51
1:02:51
PMG
19 hours ago $1.22 earnedRFK, Immigration & DeepSeek
24.6K4 -
 2:39:19
2:39:19
Scammer Payback
3 hours agoCalling Scammers Live
41.9K5