Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
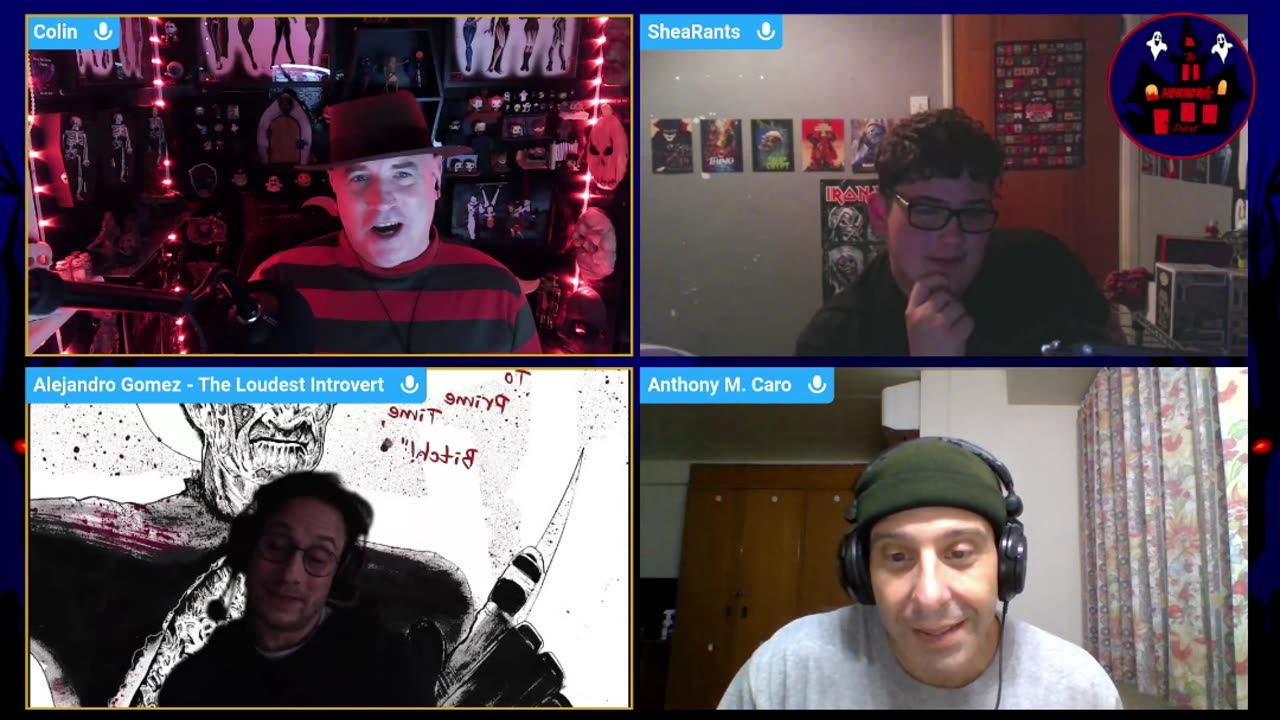
Exploring vulnerabilities
3 months ago
7
Check out the full episode here: #thehorrorificpodcast #moviereviews #nightmareonelmst #freddykrueger
https://youtube.com/live/jchIKI7I54E?feature=share
Loading comments...
-
 0:59
0:59
The HORRORific Podcast
1 month agoBygone era advertising
14 -
 LIVE
LIVE
HELMETFIRE
1 hour ago🟢Helldivers 2 🟢RUMBLE TAKEOVER!
64 watching -
 LIVE
LIVE
Precision Rifle Network
1 day agoS4E10 Guns & Grub - New Gear & 2A News
70 watching -
 LIVE
LIVE
svgames
3 hours ago🟢REPO with @soundboardlord @ZWOGs @PudgeTV @MissesMaam @Shawn Cav Live
67 watching -
 1:56:30
1:56:30
Robert Gouveia
4 hours agoTrump FIGHTS BACK in Signal Lawsuit; Judge Boasberg BLASTED; Tesla Terrorist ARRESTED!
32.2K6 -
 45:56
45:56
Michael Franzese
2 hours agoReacting to RFK Jr.'s Controversial Claims: JFK Assassination and Kennedy Legacy
23K12 -
 3:31:03
3:31:03
Barry Cunningham
5 hours agoMUST SEE: LIVE WATCH PARTY! | DOGE INTERVIEW WITH ELON MUSK! | MY MARK MITCHELL INTERVIEW!
48.3K8 -
 2:28:48
2:28:48
Rance's Gaming Corner
2 hours ago"Super Dad vs. Donkey Kong: A Mario-Sized Adventure with My Little Player One"
10K1 -
 LIVE
LIVE
megimu32
4 hours agoON THE SUBJECT: Love, Lyrics & 10 Years Later – AMA
107 watching -
 58:50
58:50
theoriginalmarkz
3 hours agoEvening News with MarkZ and Dr. Scott Young. 03/27/2025
27.4K8