Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
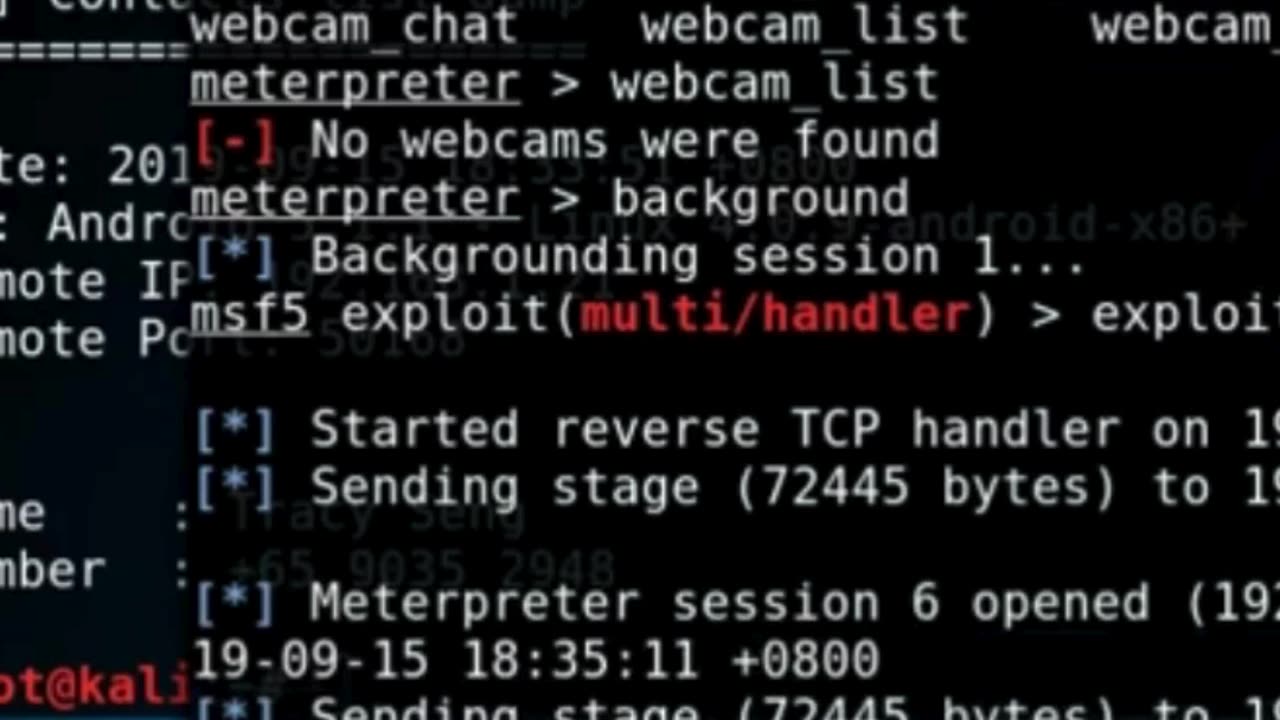
Android Device Access and Exploitation using Metasploit Kali for Cybersecurity - Tutorial Summary
8 months ago
3
Android Device Access and Exploitation using Metasploit Kali for Cybersecurity - Tutorial Summary PART 3
Loading comments...
-
 LIVE
LIVE
Vigilant News Network
14 hours agoRFK Jr. Clears Major Hurdle for HHS Secretary | The Daily Dose
843 watching -
 1:28:24
1:28:24
Game On!
15 hours ago $0.48 earnedTom Brady's SHOCKING Super Bowl Pick!
15.8K1 -
 LIVE
LIVE
Jeff Ahern
1 hour agoNever Woke Wednesday with Jeff Ahern (6am Pacific)
673 watching -
 18:52
18:52
Producer Michael
18 hours agoI GOT PULLED OVER BY THE POLICE IN MIAMI!
60.3K5 -
 1:21:53
1:21:53
MTNTOUGH Fitness Lab
23 hours agoThe Fight That Almost Destroyed Jim Miller (& How He Overcame It) to Break UFC Records
61.2K4 -
 24:46
24:46
Cooking with Gruel
1 day agoFeeding Hope - LA Wildfire Relief from the People
42.3K8 -
 14:34
14:34
MichaelBisping
15 hours agoSean Strickland CONFRONTS Bisping! 'Pereira in Corner, Dricus and Khamzat!' (EXCLUSIVE INTERVIEW)
23.9K4 -
 59:54
59:54
Trumpet Daily
22 hours ago $3.56 earnedThe Trade War Ends - Trumpet Daily | Feb. 4, 2025
22.8K25 -
 5:44
5:44
DropItLikeItsScott
15 hours ago $0.20 earnedA Must Have Shotgun - GARAYSAR Fear 116
50K5 -
 56:14
56:14
PMG
21 hours ago $0.13 earnedHannah Faulkner and John Strand | BLANKET PARDON FOR ALL J6er's
64.9K8