Premium Only Content
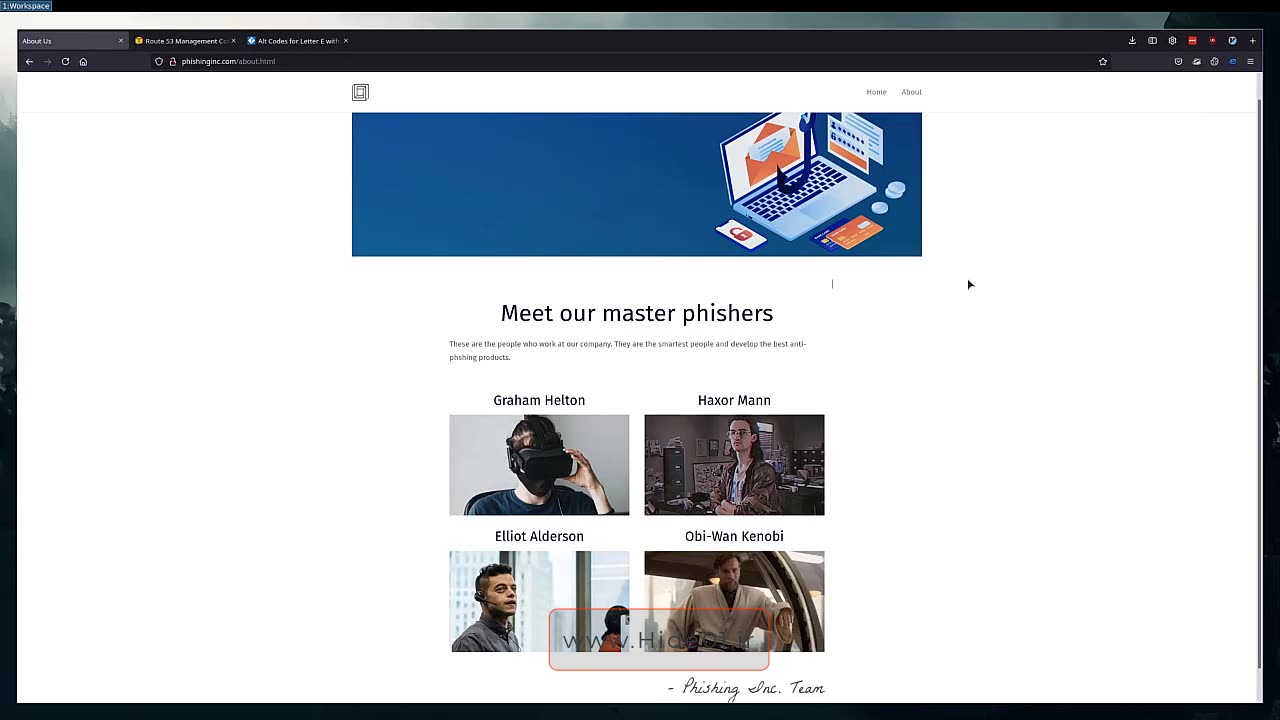
Part 2: Researching Your Target
In the second part of the practical assessment for the Phishing Assessment Course, participants delve into the critical phase of "Researching Your Target." This essential component of the course focuses on developing the skills and knowledge required to gather in-depth information about potential targets for phishing attacks.
During this phase, participants will learn how to:
Identify Target Personas: Understand the importance of profiling potential victims by their roles, responsibilities, and online presence. Recognize the significance of tailoring phishing campaigns to specific personas.
Gather Personal Information: Explore various open-source intelligence (OSINT) techniques and tools to collect data about the target, such as email addresses, social media profiles, job titles, and more.
Assess Digital Footprints: Analyze online footprints left by the target to uncover potential vulnerabilities and entry points for phishing attacks.
Social Engineering: Explore the art of social engineering and its application in crafting convincing phishing messages tailored to the target's interests, affiliations, or behaviors.
Ethical Considerations: Emphasize the importance of ethical behavior and respect for privacy laws and regulations while conducting research and crafting phishing campaigns.
By the end of Part 2, participants will have acquired the knowledge and skills necessary to comprehensively research and understand their potential phishing targets, enabling them to create more convincing and targeted phishing simulations in subsequent stages of the course. This phase ensures that ethical hackers and cybersecurity professionals are well-prepared to assess and strengthen an organization's defenses against phishing threats.
#PhishingAssessment
#CybersecurityTraining
#EthicalHacking
#InformationSecurity
#PhishingSimulation
#OnlinePrivacy
#CyberThreats
#OSINT
#SocialEngineering
#DigitalFootprint
#TargetedPhishing
#SecurityAwareness
#CyberDefense
#PhishingAwareness
#InfoSecEducation
#EthicalHacker
#CyberRisk
#DataProtection
#SecurityTraining
#CyberSkills
-
 54:30
54:30
BonginoReport
4 hours agoLeft Demands Return of MS-13 Gang Member - BR Early Edition w/ Evita (Ep.182) - 04/15/2025
94.9K83 -
 2:11:12
2:11:12
Matt Kohrs
13 hours agoMASSIVE Swings Incoming! || The MK Show
26.1K1 -
 LIVE
LIVE
Badlands Media
5 hours agoBadlands Daily: April 15, 2025
5,921 watching -
 LIVE
LIVE
The Big Mig™
3 hours agoFree Tina Peters Now! w/ Steve Stern
4,715 watching -
 LIVE
LIVE
Wendy Bell Radio
6 hours agoLiberals Love Criminal Illegals More Than They Love America
8,918 watching -
 1:15:29
1:15:29
Dear America
15 hours agoAustin Metcalf Killer RELEASED, JD Vance Fumbles CFP Trophy + CNN Gets Bullied In The Oval Office!
34.9K18 -
 LIVE
LIVE
Major League Fishing
1 day agoLIVE Tackle Warehouse Invitationals, Stop 3, Day 1
643 watching -
 55:17
55:17
2 MIKES LIVE
2 hours agoTHE MIKE SCHWARTZ SHOW with DR. MICHAEL J SCHWARTZ 04-15-2025
6.51K2 -
 1:19:29
1:19:29
Game On!
14 hours ago $4.56 earned8,000 Subscriber Celebration Stream!
40.3K2 -
 28:30
28:30
Degenerate Jay
16 hours ago $4.36 earnedThe Rejected 007 Quantum Of Solace Ending That Would Have Changed James Bond
56.5K6