Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
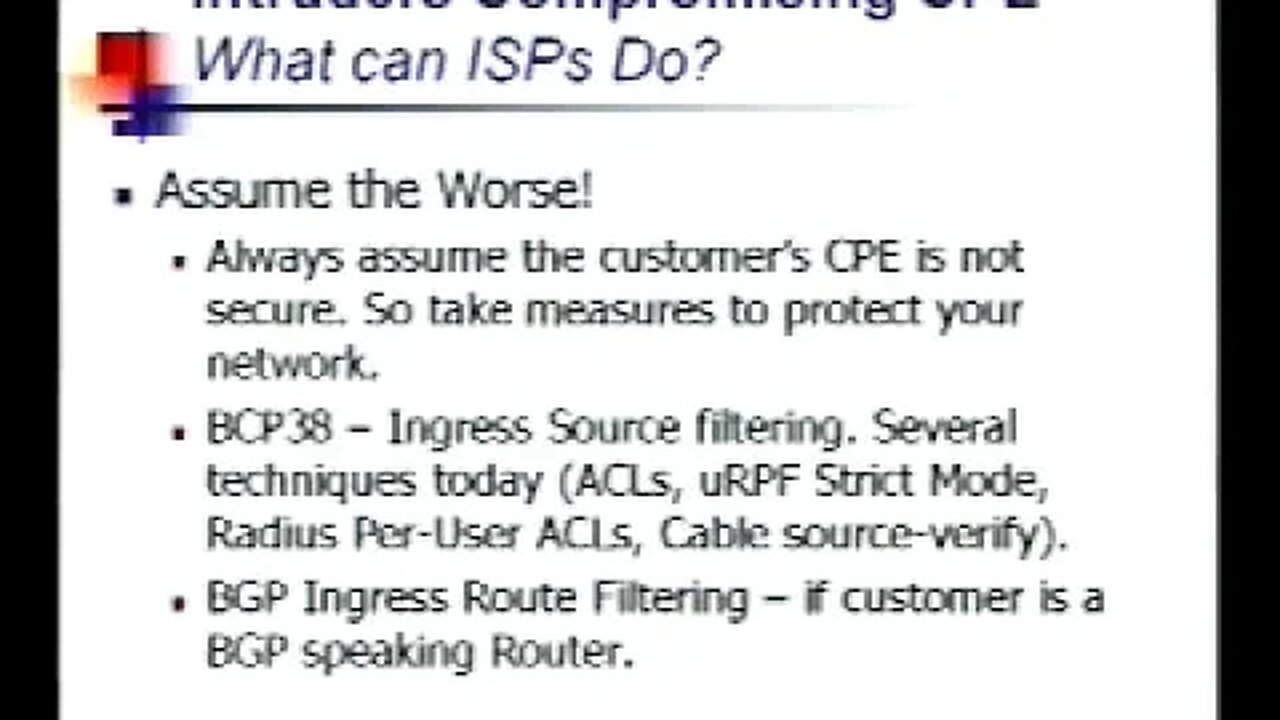
Tutorial ISP Security Real World Techniques II
Repost
Loading comments...
-
 33:47
33:47
Stephen Gardner
6 hours ago🔥Pentagon Whistleblower UNLEASHES on Biden and Obama!
48.4K43 -
 2:20:30
2:20:30
The Dilley Show
7 hours ago $19.11 earnedRoger Stone in Studio plus Q&A Friday! w/Author Brenden Dilley 12/27/2024
49.3K7 -
 1:57:02
1:57:02
The Charlie Kirk Show
5 hours agoThe Great H-1B Battle + AMA | Lomez | 12.27.24
120K111 -
 11:39
11:39
Russell Brand
1 day agoWhat You're Not Being Told About The Syrian War
140K217 -
 LIVE
LIVE
Bannons War Room
1 year agoWarRoom Live
9,549 watching -
 1:49:21
1:49:21
Film Threat
8 hours agoBEST AND WORST OF 2024 + SQUID GAME SEASON 2 | Film Threat Livecast
46.9K5 -
 1:06:04
1:06:04
The Big Mig™
22 hours agoGlobal Finance Forum Powered By Genesis Gold Group
39.4K2 -
 34:38
34:38
Tudor Dixon
6 hours agoThe Changing Landscape Between Tech and Politics with Mike Benz | The Tudor Dixon Podcast
30K4 -
 2:23:58
2:23:58
Matt Kohrs
17 hours agoRumble's Stock Is EXPLODING!!! || The MK Show
86K8 -
 1:57:47
1:57:47
LFA TV
20 hours agoBOMBSHELL FINAL REPORT: BIDEN ADMIN SUPPRESSED WUHAN LAB LEAK | LIVE FROM AMERICA 12.27.24 11am EST
52.1K6