Premium Only Content
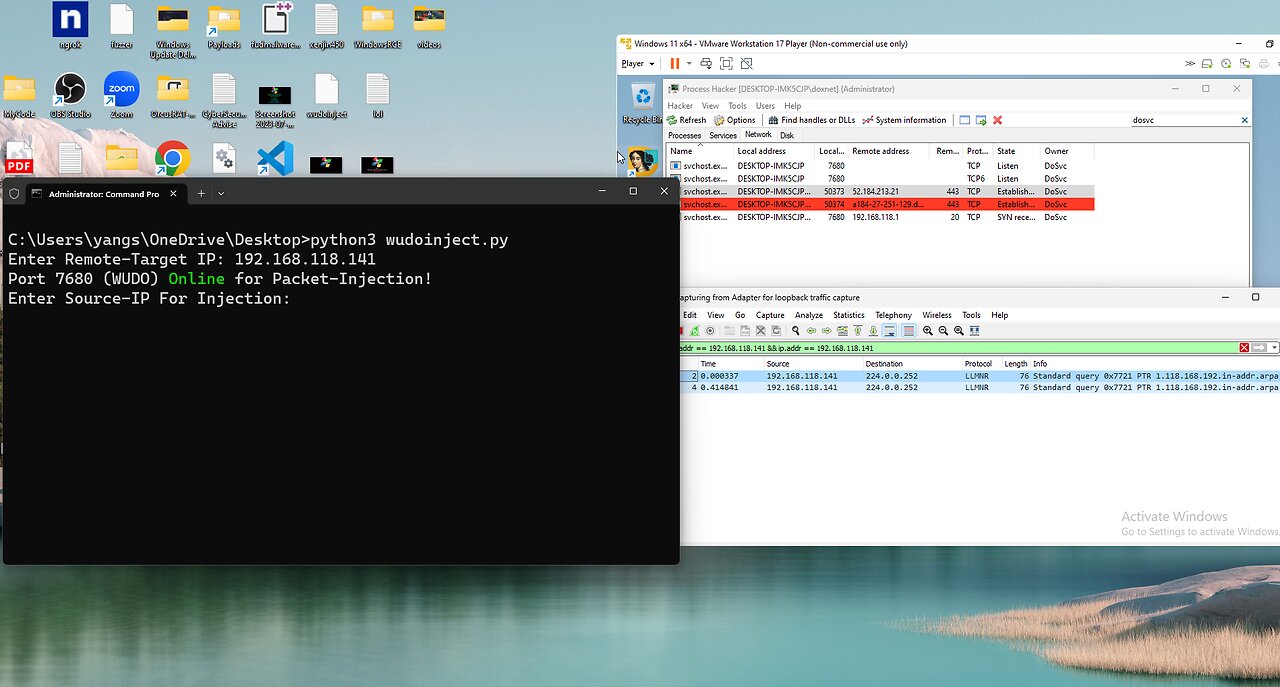
Windows 11 Remote Security-Testing/Fuzzing
Windows 11 Remote Security-Testing/Reverse-Engineering
I Injected A Spoofed Crafted Packet That I Programmed Myself To Sent Remotely Over The Network Into The Remote Windows 11 System , It Reached The loopback-interface Which Is Commonly Used For Applications/Services Communication on eachother inside the Windows System . And the Inbound Ports that are Filtered By The Firewall are also inside that specific Internal System Network Communication Segment . But I Bypassed It To Land A Packet Inside Internally And Triggered Some Interesting Responses Which Would Also Show On The DoSvc (Windows Update Delivery Optimization Port 7680) Service . That Triggered The IP Adress And Port 7680 To Reach A Remote IP/Port Adress Which I Can Specify To Spoof . So This Is In Development Still For Security Testing And Finding Bugs . I Will Go Into More Of It Persistently. Maybe Modification On The Packet Could Lead To ( RCE Remote Code Execution) On The Remote Target System.
#exploitdevelopment #exploit #zeroday #vulnerability #networking #network #windows11 #windows #system #systems #cybersecurity #security #securitytesting #hacker #hacking #hack #remote #injection #packet #wireshark #traffic #data #technology #digital #it #port #scanning
-
 2:08:19
2:08:19
Tactical Advisor
15 hours agoThe Vault Room Podcast 006 | Farwell 2024 New Plans for 2025
173K11 -
 34:12
34:12
inspirePlay
1 day ago $5.09 earned🏆 The Grid Championship 2024 – Cass Meyer vs. Kelly Rudney | Epic Battle for Long Drive Glory!
75.9K8 -
 17:50
17:50
BlackDiamondGunsandGear
12 hours ago $1.91 earnedTeach Me How to Build an AR-15
50.7K6 -
 9:11
9:11
Space Ice
1 day agoFatman - Greatest Santa Claus Fighting Hitmen Movie Of Mel Gibson's Career - Best Movie Ever
110K47 -
 42:38
42:38
Brewzle
1 day agoI Spent Too Much Money Bourbon Hunting In Kentucky
74K12 -
 1:15:30
1:15:30
World Nomac
21 hours agoMY FIRST DAY BACK in Manila Philippines 🇵🇭
57K9 -
 13:19
13:19
Dr David Jockers
1 day ago $10.86 earned5 Dangerous Food Ingredients That Drive Inflammation
76.5K17 -
 1:05:13
1:05:13
FamilyFriendlyGaming
1 day ago $15.76 earnedCat Quest III Episode 8
129K3 -
 10:39
10:39
Cooking with Gruel
2 days agoMastering a Succulent London Broil
82.8K5 -
 22:15
22:15
barstoolsports
1 day agoWhite Elephant Sends Barstool Office into Chaos | VIVA TV
58.3K1