Premium Only Content
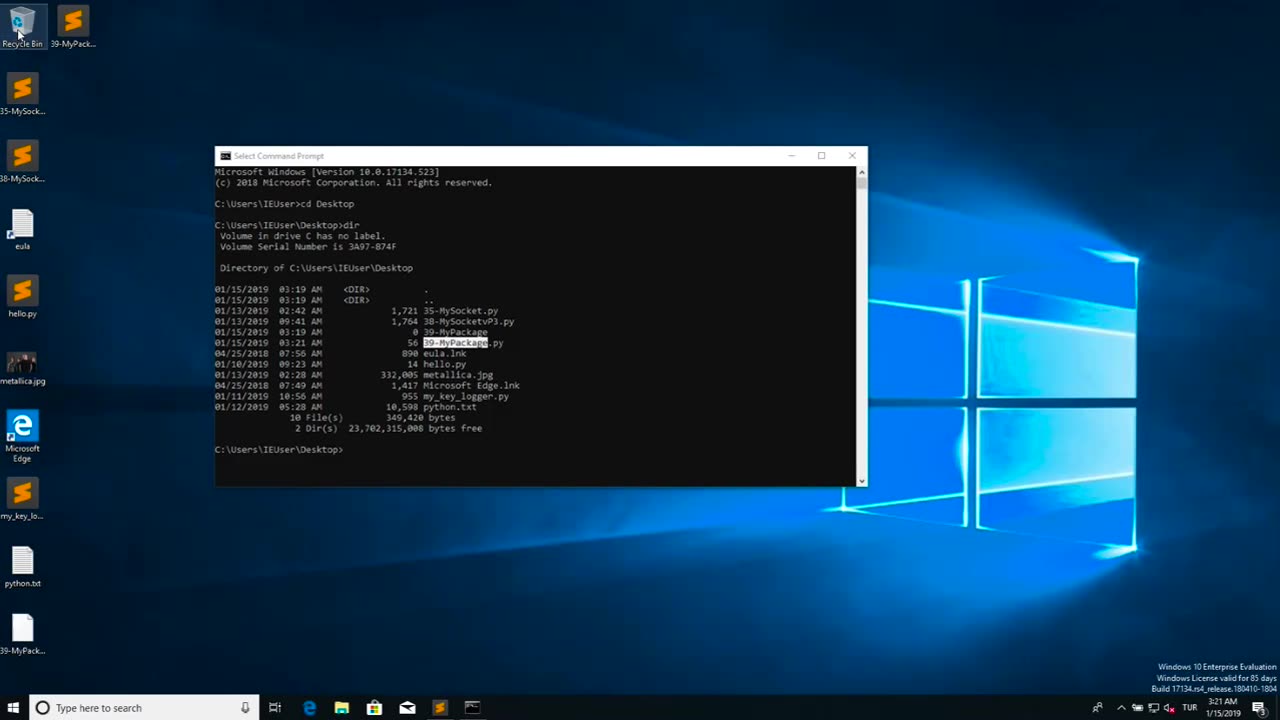
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 1:03:27
1:03:27
Glenn Greenwald
6 hours agoUK Pressures Apple to Break Encryption in Major Privacy Clash; How Dems Can Win Back the Working Class: With Former Bernie Sanders Campaign Manager Faiz Shakir | SYSTEM UPDATE #419
37.8K43 -
 47:39
47:39
Michael Franzese
4 hours agoJewelry King Trax NYC EXPOSES How the Powerful Steal from You
45.3K10 -
 LIVE
LIVE
Slightly Offensive
4 hours ago $2.86 earnedCandace REDPILLS the Masses in BOMBSHELL Theo Von Interview | Guest: Shane Cashman
1,377 watching -
 UPCOMING
UPCOMING
DLDAfterDark
29 minutes agoDLD Live! That Sh... Will Get You K***ed! What To Consider in SHTF
-
 LIVE
LIVE
megimu32
3 hours agoON THE SUBJECT: IRL Streamers Attacked & Nostalgic Animal Movies That Made Us Cry
442 watching -
 1:00:54
1:00:54
The Tom Renz Show
7 hours agoMore Epstein/FBI, a Scary Trade War, & the Dem Echo Chamber
7.49K1 -
 40:43
40:43
Kimberly Guilfoyle
8 hours agoDems Double Down on Delusion-Why? Live with Tony Kinnett & Bo French | Ep.202
77.8K35 -
 1:28:42
1:28:42
Redacted News
6 hours agoBREAKING! SOMETHING BIG IS HAPPENING IN EUROPE ALL OUT WAR IS COMING AGAINST RUSSIA, TRUMP FURIOUS
121K287 -
 47:50
47:50
Candace Show Podcast
6 hours agoBREAKING: Judge Makes Statement Regarding Taylor Swift's Text Messages. | Candace Ep 155
113K117 -
 1:14:23
1:14:23
Josh Pate's College Football Show
3 hours ago $0.29 earnedCFB’s Most Hated Teams | FSU & Clemson Future | Big Ten Win Totals | Star Rankings Overrated?
14.5K