Premium Only Content
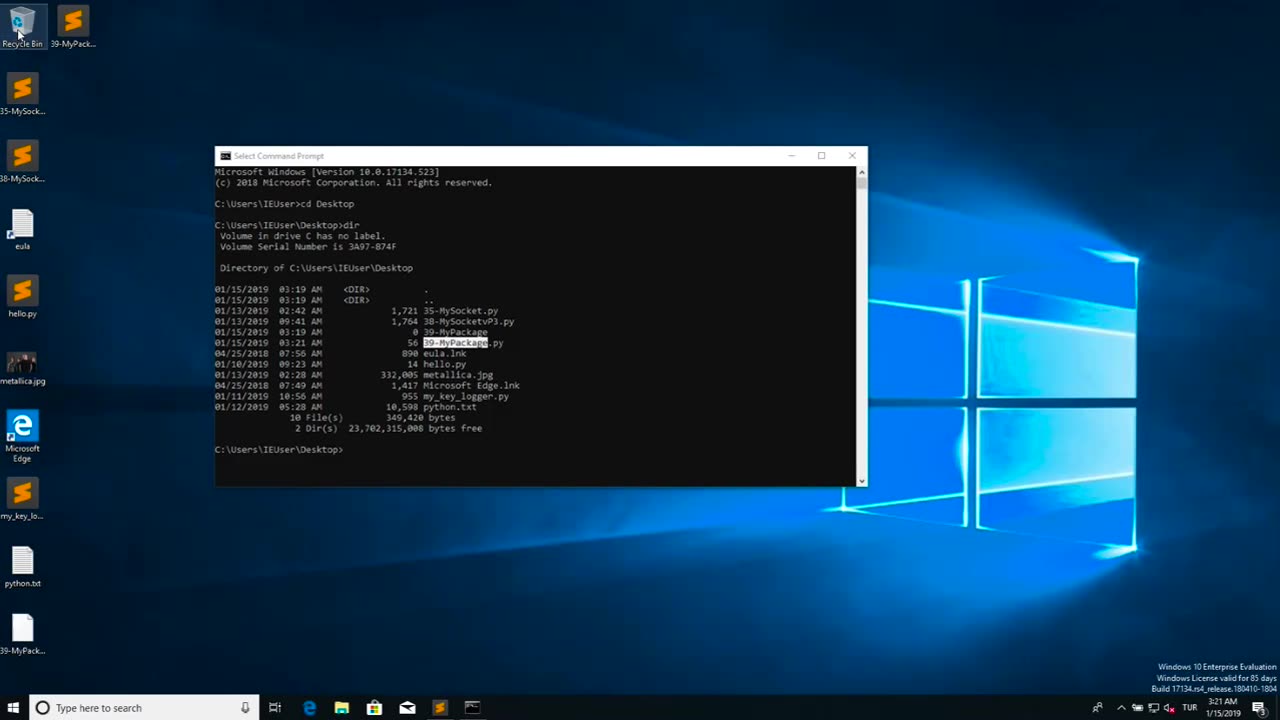
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 1:45:39
1:45:39
Kim Iversen
6 hours agoTrump Attacks Thomas Massie—But MAGA Isn’t Having It! Is Trump Picking the Wrong Fight?
41.8K77 -
 56:31
56:31
Glenn Greenwald
5 hours agoUNLOCKED EPISODE: On Europe’s Emergency Defense Summit, the Future of Independent Media, Speech Crackdowns and More
90.8K45 -
 43:48
43:48
BonginoReport
7 hours agoMainstream Media Plots The Next Plandemic! (Ep.02) - 03/11/2025
126K254 -
 1:13:13
1:13:13
Michael Franzese
7 hours agoMegyn Kelly’s UNFILTERED Take on The Ukraine War, Trump & Modern Masculinity
90.8K36 -
 1:43:21
1:43:21
Redacted News
8 hours agoBREAKING! UKRAINE AGREES TO CEASEFIRE WITH RUSSIA... BUT THERE'S A BIG CATCH | Redacted News
172K302 -
 58:17
58:17
Candace Show Podcast
9 hours agoShould We Feel Bad For Blake Lively? | Candace Ep 157
139K283 -
 3:06:52
3:06:52
The Nerd Realm
9 hours ago $11.46 earnedHollow Knight Voidheart Edition #19 | Nerd Realm Playthrough
84.4K6 -
 1:17:27
1:17:27
Awaken With JP
12 hours agoThe Current Thing: Tesla Protesting - LIES Ep 82
146K75 -
 1:07:08
1:07:08
Sean Unpaved
9 hours agoNFL Free Agency Rolls On! MLB Spring Training Heats Up along with 3x World Series Champ Dave Stewart
87.6K3 -
 2:10:15
2:10:15
Right Side Broadcasting Network
14 hours agoLIVE REPLAY: White House Press Secretary Karoline Leavitt Holds Press Briefing - 3/11/25
174K43