Premium Only Content
Chapter-38, LEC-11 | Sending Commands With List | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
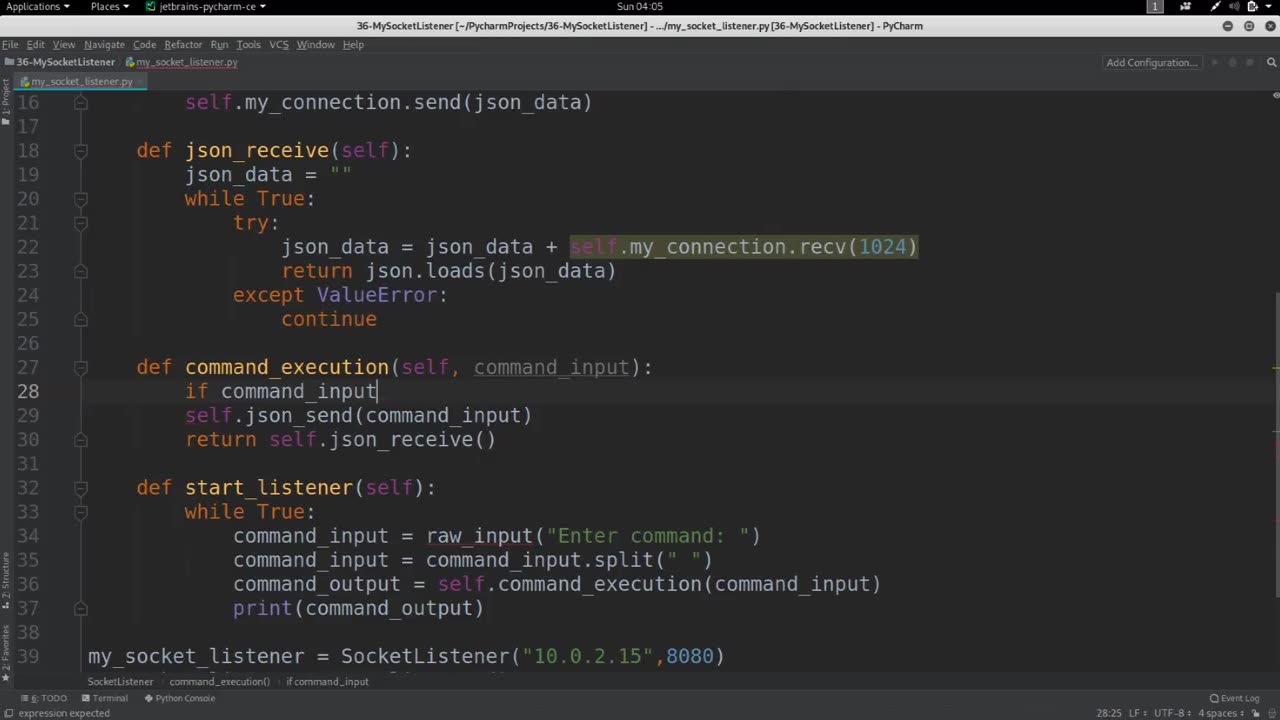
Sending commands with a list refers to the practice of sending a list of commands or instructions from one system or application to another for execution or processing. This can be done in various contexts, such as in computer programming, automation, or remote communication between systems.
When sending commands with a list, a typical workflow may involve the following steps:
Creating a list: A list is created to store the commands or instructions that need to be sent. A list is a data structure that can hold multiple items or elements in a specific order, and it can be of fixed or dynamic size depending on the programming language or application being used.
Adding commands to the list: Commands or instructions are added to the list, typically as individual elements. These commands can be represented as strings, objects, or any other data type that is appropriate for the specific application or system. The list can be modified by appending, inserting, or updating elements as needed.
Sending the list: The list of commands is then sent or transmitted to the receiving system or application. This can be done through various communication methods, such as APIs, sockets, HTTP requests, or other protocols depending on the system architecture and requirements.
Receiving and processing the list: The receiving system or application retrieves the list of commands and processes each command sequentially or in parallel, depending on the implementation. The commands are executed or interpreted according to their intended purpose, which could be performing actions, making decisions, updating data, or triggering specific functionalities.
Error handling: Proper error handling techniques should be implemented to handle any potential errors that may occur during the sending or processing of the list of commands. This can include checking for invalid commands, handling timeouts, managing exceptions, and providing appropriate feedback or error messages to the sender or end users.
Sending commands with a list can be a powerful way to communicate and automate tasks between systems or applications. It allows for flexibility in specifying multiple commands in a single transmission, enabling efficient and streamlined communication and automation workflows. Properly designing and implementing the list of commands, along with robust error handling, can help ensure reliable and secure command execution in various systems and applications.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 1:33:58
1:33:58
Right Side Broadcasting Network
5 hours agoLIVE REPLAY: President Trump Greets Ohio State National Football Champions at the White House - 4/14/25
13.5K2 -
 LIVE
LIVE
KingB33Gaming
14 hours agoZero Sum Seattle - Tommy is Still Missing | The Last Of Us PT 2 Remastered
340 watching -
 1:29:08
1:29:08
Dabkillah
1 hour ago🔴LIVE-DABKILLAH MONDAY BLAH HAHAHAH
2.78K -
![[Ep 649] The Border is SEALED! | Real ID: Freedom’s Shield or Surveillance Trap?](https://1a-1791.com/video/fww1/46/s8/1/B/3/8/B/B38By.0kob-small-Ep-649-The-Border-is-SEALED.jpg) LIVE
LIVE
The Nunn Report - w/ Dan Nunn
1 hour ago[Ep 649] The Border is SEALED! | Real ID: Freedom’s Shield or Surveillance Trap?
150 watching -
 1:49:02
1:49:02
Russell Brand
4 hours agoTrump THREATENS China “NOBODY is getting off the hook” As Trade War INTENSIFIES! – SF565
131K32 -
 1:04:26
1:04:26
Sean Unpaved
4 hours agoRory's Masters Glory!, NBA Play-Ins Preview, Tennessee Moving On From Iamaleava?
40.1K -
 9:00
9:00
Film Threat
5 hours agoWARFARE | Film Threat Reviews
18.7K7 -
 1:04:04
1:04:04
Timcast
4 hours agoDemocrat Governor's Home FIREBOMBED, Liberal's Luigi Mangione Effect Driving INCREASE In Violence
188K169 -
 1:57:44
1:57:44
Steven Crowder
7 hours ago🔴 The Most Un-American School Suspension of All Time & The New Worst City in America
406K323 -
 2:05:42
2:05:42
Nerdrotic
8 hours ago $4.50 earnedHarry Potter Casts BLACK Snape | Dr Who Hits New LOW - Nerdrotic Nooner 479
88.9K32