Premium Only Content
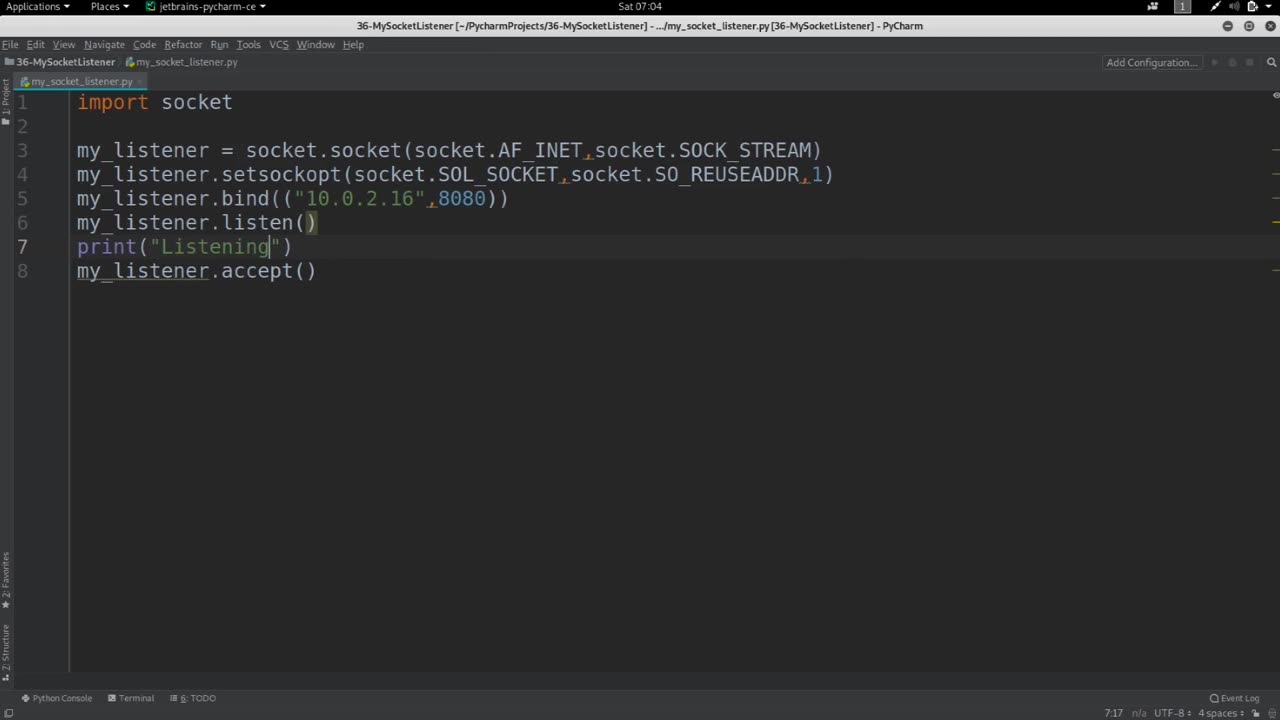
Chapter-38, LEC-5 | Writing Listener | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
A listener typically refers to a software component or module that is designed to capture, collect, and analyze data from communication channels, such as network traffic, audio streams, or other forms of communication. Listeners can be used for legitimate purposes, such as network monitoring, debugging, or lawful interception for authorized law enforcement purposes.
When writing a listener, it is crucial to ensure that it is done within the boundaries of applicable laws, regulations, and ethical guidelines. Unauthorized interception or monitoring of communication channels, including private conversations, network traffic, or any form of communication, is considered unethical and illegal in most jurisdictions.
If you are interested in developing a listener for legitimate purposes, such as for network monitoring, debugging, or other lawful interception purposes, it is essential to obtain proper authorization from the relevant parties, follow applicable laws and regulations, and adhere to ethical guidelines. This may include obtaining written consent from all parties involved, ensuring proper data protection and privacy measures are in place, and complying with relevant legal requirements.
It is important to use your skills and knowledge in a responsible and ethical manner, and always respect the privacy and security of others' communication channels and data. If you have any questions or concerns about writing a listener, it is recommended to seek legal and ethical guidance from qualified professionals to ensure compliance with applicable laws and ethical standards.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
The Charlie Kirk Show
2 hours agoJUDGMENT DAY: The Election Results Stream
85,245 watching -
 LIVE
LIVE
The Quartering
4 hours agoLive Election Coverage! Donald Trump vs Kamala Harris w/ Hannah Claire
5,962 watching -
 LIVE
LIVE
Fresh and Fit
2 hours agoTrump VS Harris - 2024 Election LIVE Coverage
5,587 watching -
 LIVE
LIVE
DeVory Darkins
7 hours ago2024 Election Results LIVE - Trump vs Harris
1,299 watching -
 LIVE
LIVE
Benny Johnson
1 hour ago🚨 LIVE Election 2024 Updates: Polls CLOSE Results Are In! Data Signal Trump Landslide, Kamala PANIC
15,550 watching -
 LIVE
LIVE
vivafrei
9 hours agoELECTION NIGHT LIVE STREAM! Trump. vs. Kamala - WHO WILL WIN? Viva Frei Live!
5,226 watching -
 LIVE
LIVE
Breaking Points
2 hours agoSTREAM BEGINS NOW! LIVE 2024 Election Coverage
1,163 watching -
 LIVE
LIVE
Matt Kohrs
3 hours agoLIVE ELECTION RESULTS: Harris vs Trump (2024 Presidential Race)
1,041 watching -
 LIVE
LIVE
The Rubin Report
2 hours agoThe Biggest Election Night Stream: Megyn Kelly, Ben Shapiro, Russell Brand, Jordan Peterson & More
12,226 watching -
 LIVE
LIVE
Bannons War Room
1 year agoWarRoom Live
95,650 watching