Premium Only Content
Chapter-35, LEC-2 | MITM Refreshed | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
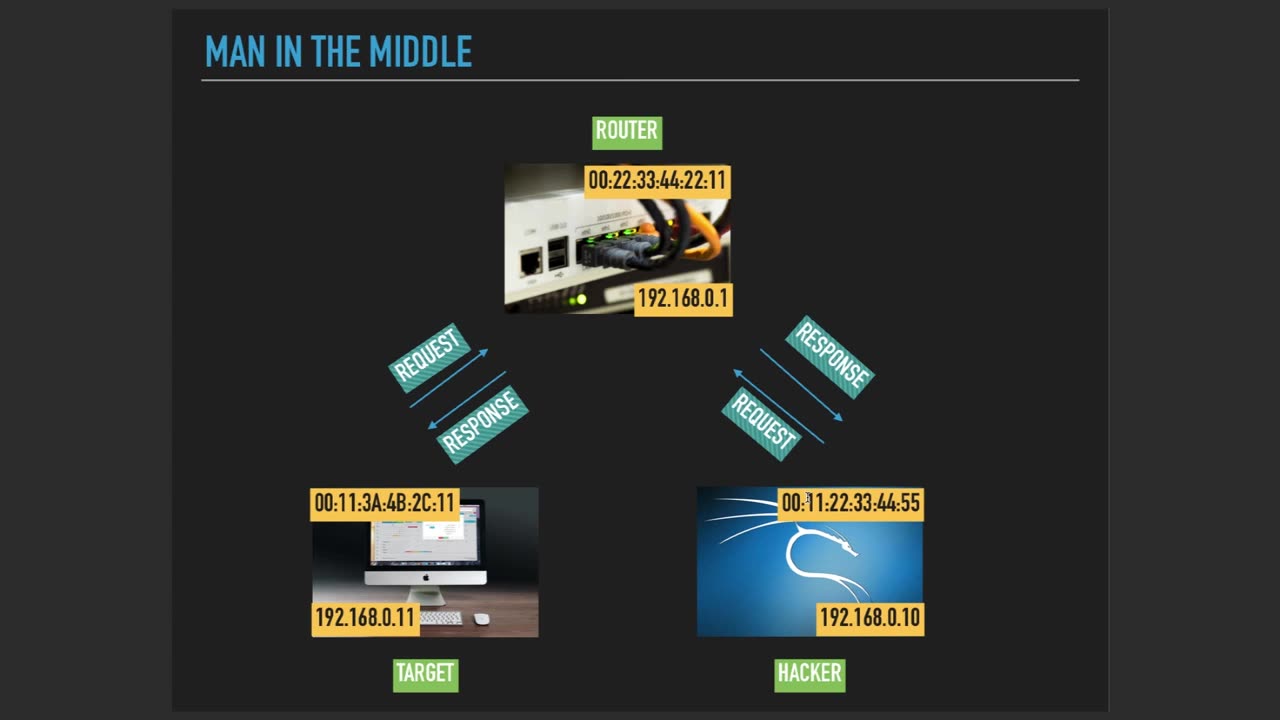
MITM Refreshed is a modern and sophisticated variation of the traditional Man-in-the-Middle (MITM) attack, which is a type of cyber attack that intercepts communication between two parties. In a MITM Refreshed attack, the attacker employs advanced techniques and tools to circumvent modern security measures and gain unauthorized access to sensitive information.
Unlike traditional MITM attacks, which may rely on known vulnerabilities or basic spoofing techniques, MITM Refreshed attacks often utilize sophisticated methods, such as zero-day exploits, advanced social engineering, or complex malware, to intercept and manipulate communication. This makes them highly effective and challenging to detect.
In a MITM Refreshed attack, the attacker may target various communication channels, including wired or wireless networks, web applications, email systems, or even encrypted connections. By positioning themselves between the legitimate parties, the attacker can stealthily monitor, modify, or inject malicious data into the communication without raising suspicion.
The consequences of a MITM Refreshed attack can be severe, as it can lead to data breaches, financial loss, reputational damage, and legal repercussions. Organizations and individuals must employ robust security measures, such as multi-factor authentication, encryption, intrusion detection systems, and regular security audits, to defend against MITM Refreshed attacks. Ongoing training and awareness programs to educate users about the risks and best practices for securely communicating and transmitting sensitive information are also critical in mitigating the threat of MITM Refreshed attacks.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Donald Trump Jr.
4 hours agoOne Week Until Inauguration, Live with Rep Anna Paulina Luna & Sen Tommy Tuberville
5,489 watching -
 LIVE
LIVE
The Jimmy Dore Show
21 minutes agoConfronting LIES About January 6th! LA Fire Chief KNEW About Empty Reservoirs! w/ Greg Foreman
4,501 watching -
 LIVE
LIVE
Dr Disrespect
7 hours ago🔴LIVE - DR DISRESPECT - MARVEL RIVALS - TOP 500 IN THE WORLD
2,804 watching -
 LIVE
LIVE
SpartakusLIVE
35 minutes ago#1 Hacker/Scammer PLUNGES into CRYPTO || !crypto !spartacoin
205 watching -
 53:15
53:15
Kimberly Guilfoyle
4 hours agoCalifornia Residents Demand Answers, Live with Rep Vince Fong, Mike Davis, and Paul Peterson | Ep. 188
20.5K39 -
 1:49:51
1:49:51
Redacted News
3 hours agoEMERGENCY! 10 MILLION UNDER FIRE WARNING & 100 MPH WINDS, NEWSOM UNVEILS CALIFORNIA 2.0 PLAN
71.3K103 -
 49:33
49:33
Candace Show Podcast
2 hours agoI Respond To Mr. And Mr. Macron | Candace Ep 131
48.6K118 -
 1:58:04
1:58:04
Revenge of the Cis
4 hours agoEpisode 1429: Catch And Release
15.4K1 -
 2:00:01
2:00:01
Film Threat
8 hours agoVERSUS: HOLLYWOOD IS STILL ON FIRE | Film Threat Versus
7.26K -
 12:33
12:33
Silver Dragons
3 hours agoSilver Price Crushed Today - NEW TREND STARTING?
7.47K