Premium Only Content
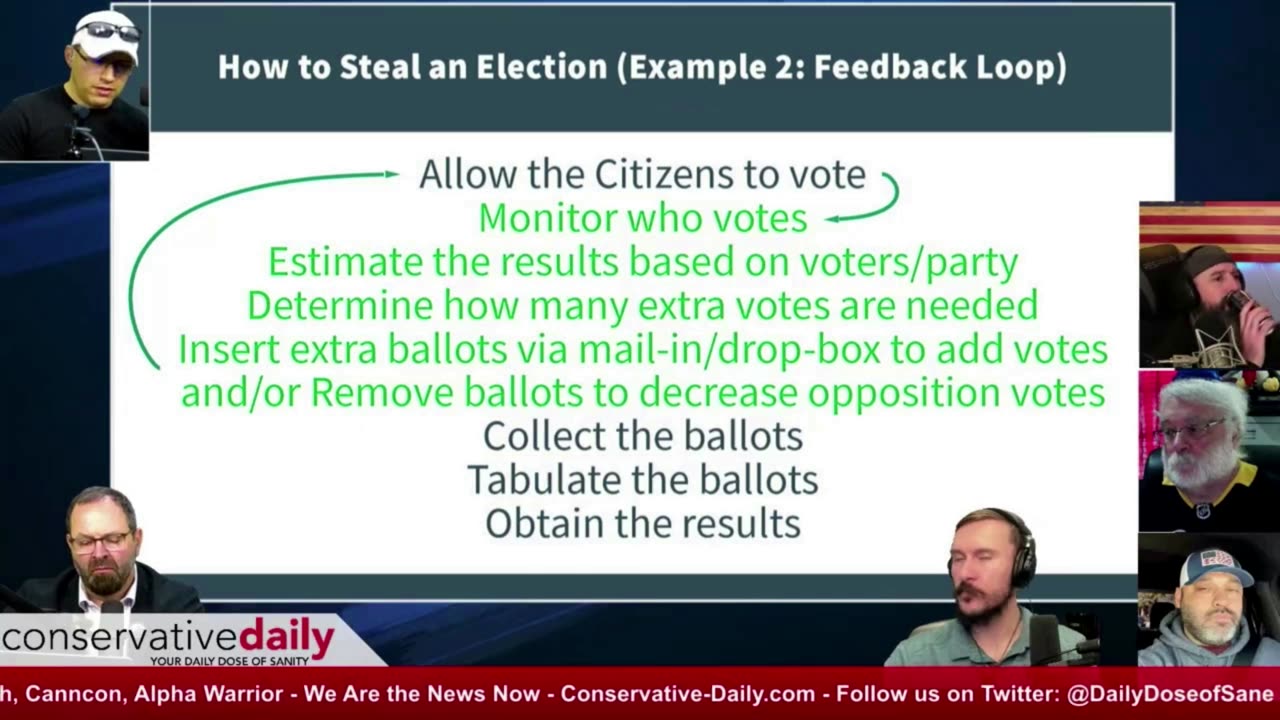
PART 2 - How to Steal an Election | Election Theft 2020
Watching Part 1 of How to Steal an Election is required before viewing Part 2 in order to understand the context of Part 2. Is election theft possible? Yes. The video goes back to a 2004 congressional testimony from Clint Curtis - a programmer who wrote an algorithm and code to steal an election on behalf of Republican Tom Feeny in Florida. From that point, programmers have had more than 20 years to improve, hide, and master the code required to manipulate the voting machines commonly used in elections today. Here, A panel of professional Software and IT Guys discuss how the 2020 Election was stolen. In this video, you'll see how using simple batch files (invisible commands to the computer that are executed automatically) from a simple flash drive to the Microsoft SQL Database Server can switch election results in less than 1 minute. MS SQL Server is found on every voting machine - put there by every voting machine manufacturer. Additionally, every Dell motherboard in the voting machines contains a wireless modem (enabling remote communications) with additional communication ports built into the board - ordered by Dominion Voting Systems (and other manufacturers). The video describes the accessibility vulnerabilities of Dominion's (and most company) Voting Machine Equipment and how they can be exploited by bad actors and even honest people with little to no knowledge that they are participating in the election theft. Part 2 of the video drills deeply into the election attack plans already being implemented and concludes with the notion that there is no fix to the election machine problem - all machines must go. However, the panel presents an outstanding way to conduct elections without the use of any election equipment that should be implemented by every county in the USA as a matter of course. The video is a must-see for every election official and informed American citizen.
-
 LIVE
LIVE
2 MIKES LIVE
1 hour ago2 MIKES LIVE #158 Government Shutdown Looms and Games!
193 watching -
 LIVE
LIVE
The Big Mig™
5 hours agoVeteran, Patriot, Leader, Author Allen West joins The Big Mig Show
218 watching -
 LIVE
LIVE
The Amber May Show
21 hours agoBloated CR Failed | What Did The View Say Now? | Who Kept Their Job At ABC| Isaac Hayes
118 watching -
 59:29
59:29
State of the Second Podcast
4 days agoAre We Losing the Fight for Gun Rights? (ft. XTech)
6.03K3 -
 1:00:10
1:00:10
The Nima Yamini Show
2 hours agoTragedy in Germany 🇩🇪 Suspected Terror Attack at Christmas Market – LIVE Updates from Germany
15K18 -
 10:52
10:52
Evenout
2 hours ago $0.45 earnedTIME TRAVELLING ON THE ESCALATOR TWIN PRANK!
6.31K2 -
 5:43:44
5:43:44
Scammer Payback
7 hours agoCalling Scammers Live
78.4K12 -
 LIVE
LIVE
Barry Cunningham
4 hours agoWATCH LIVE: James O'Keefe, Gen. Michael Flynn,, Byron Donalds, PBD & More At AmericaFest!
878 watching -
 2:00:10
2:00:10
Twins Pod
7 hours agoYouth Pastor Confronts People Possessed By DEMONS! | Twins Pod - Episode 44 - Drew Hernandez
44.5K12 -
 1:37:40
1:37:40
The Quartering
7 hours agoShutdown Watch, Biden Dementia Bombshell, Madison Shooter Had An Accomplice & Much More!
83.5K36