Premium Only Content
Chapter-29, LEC-2 | Useful Methods #hacking #growthhacking #ethicalhacking #rumble #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking
It is a crucial part of cybersecurity and helps organizations in protecting their sensitive information from malicious attackers.
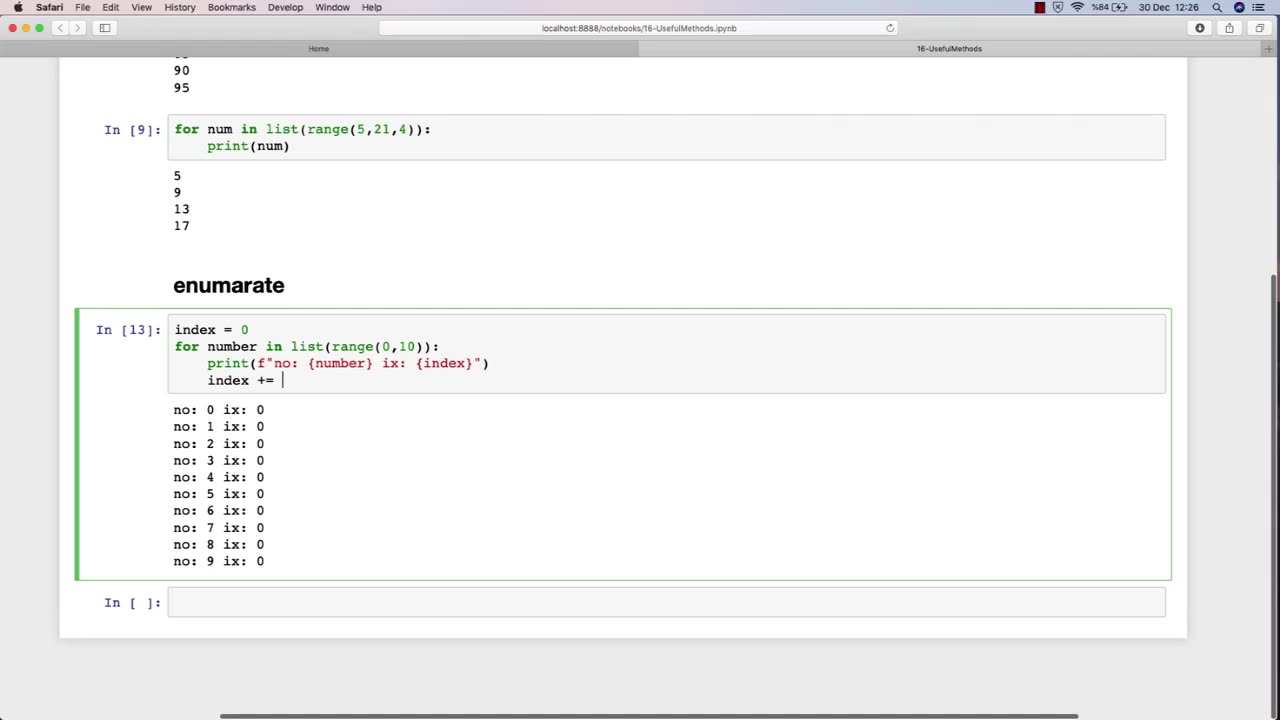
One of the most essential topics in an ethical hacking course is the use of various methods and tools for conducting effective security assessments. One such useful method is the use of penetration testing.
Penetration testing is a simulated attack on a computer system or network to identify vulnerabilities that a malicious attacker could exploit. This method involves using various hacking techniques and tools to try to gain access to the system or network. Penetration testing is a comprehensive approach to testing a system's security and can help identify potential weaknesses that can be addressed before they can be exploited by malicious attackers.
Another important topic in an ethical hacking course is the use of vulnerability scanners. Vulnerability scanners are automated tools that scan a computer system or network to identify vulnerabilities that can be exploited by attackers. These tools can help identify issues such as outdated software, weak passwords, and misconfigured settings.
Social engineering is another useful method that ethical hackers use to identify vulnerabilities in a system or network. Social engineering involves manipulating individuals into divulging sensitive information or performing actions that can compromise the security of a system. This technique can help identify weaknesses in an organization's security policies and training programs.
Overall, ethical hacking courses teach various methods and techniques that can be used to identify vulnerabilities in computer systems and networks. By using these methods, ethical hackers can help organizations strengthen their security measures and protect their sensitive information from malicious attackers.
-
 1:32:34
1:32:34
Glenn Greenwald
3 hours agoThe Future of Gaza With Abubaker Abed; Journalist Sam Husseini On His Physical Expulsion From Blinken’s Briefing & Biden’s Gaza Legacy | System Update #391
36.1K45 -
 1:34:48
1:34:48
Roseanne Barr
5 hours ago $7.13 earnedWe are so F*cking Punk Rock! with Drea de Matteo | The Roseanne Barr Podcast #83
30.3K26 -
 LIVE
LIVE
Man in America
6 hours ago🇨🇳 RedNote: A CCP Trojan Horse Deceiving Americans? w/ Levi Browde
563 watching -
 LIVE
LIVE
I_Came_With_Fire_Podcast
9 hours agoTrump SABOTAGE, LA FIRE CHIEF SUED, and BIDEN’S LAST F-U!
135 watching -
 LIVE
LIVE
Joker Effect
1 hour agoUkraine in a video game? Hardest thing I have done. S.T.A.L.K.E.R.2 Heart of Chornobyl,
515 watching -
 LIVE
LIVE
Flyover Conservatives
21 hours agoEczema, Brain Fog, B.O., and Gas… Eating Steak and Butter Creates Ultimate Health Hack - Bella, Steak and Butter Gal | FOC Show
526 watching -
 51:58
51:58
PMG
4 hours ago"Can the Government Learn from Elon Musk’s 70% Labor Cut? A Deep Dive into Inefficient Agencies"
562 -
 LIVE
LIVE
Amish Zaku
4 hours agoRumble Spartans #10 - New Year New Maps
94 watching -
 1:04:58
1:04:58
In The Litter Box w/ Jewels & Catturd
1 day agoNo Tax On Tips! | In the Litter Box w/ Jewels & Catturd – Ep. 722 – 1/17/2025
127K31 -
 5:35:39
5:35:39
Dr Disrespect
10 hours ago🔴LIVE - DR DISRESPECT - WARZONE - CRAZY CHALLENGES
153K33