Premium Only Content
Chapter-17, LEC-4 | Downloading Files | #ethicalhacking #cybersport #cybersecurity
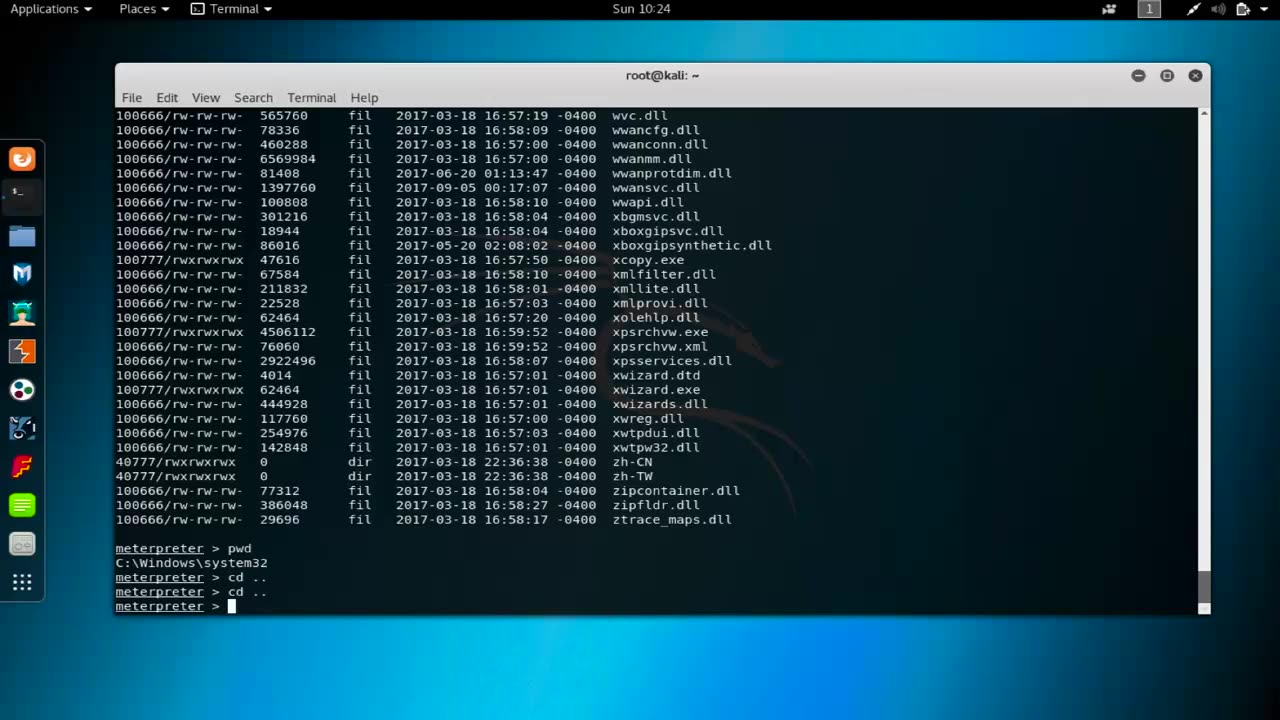
Downloading files is a common post-hacking session technique that is used to extract sensitive data or other valuable information from a compromised system or network. This technique is often used by attackers to exfiltrate stolen data or to download additional tools or payloads onto the compromised system.
When an attacker gains access to a system using a Meterpreter payload or other post-exploitation tool, they can use various techniques to download files from the compromised system. For example, they can use the "download" command in Meterpreter to transfer specific files or folders to the attacker's machine. Alternatively, they can use other tools, such as FTP or SCP, to copy files to a remote server or cloud storage service.
Downloading files can be a time-consuming process, especially if the target system contains large amounts of data. To speed up the process, attackers may use compression tools like "tar" or "zip" to bundle multiple files or folders together and transfer them in a single archive. They may also use network-level techniques like port-forwarding or VPNs to bypass firewalls or other security measures that may block the transfer of files.
Downloading files can be a risky post-hacking session technique because it leaves traces of the attacker's activities on the compromised system, making it easier for security teams to detect and investigate the breach. As such, attackers may use various tactics to obfuscate their activities, such as deleting logs or using encryption to hide the data that is being exfiltrated.
Overall, downloading files is a powerful post-hacking session technique that can allow attackers to exfiltrate sensitive data or download additional tools or payloads onto the compromised system. However, it is also a high-risk technique that requires careful planning and execution to avoid detection and ensure a successful breach.
-
 LIVE
LIVE
The White House
1 hour agoPress Secretary Karoline Leavitt Briefs Members of the New Media, Apr. 29, 2025
2,099 watching -
 1:18:15
1:18:15
The Rubin Report
1 hour agoPress Gasps When Told Trump’s Executive Order for Sanctuary Cities
13.8K29 -
 LIVE
LIVE
Flyover Conservatives
11 hours agoThe Future of AI: The Good, The Bad, The Ugly - Marc Beckman | FOC Show
193 watching -
 LIVE
LIVE
The Shannon Joy Show
2 hours ago🔥🔥Doctors Of Death. The Transformation Of America’s Health System Into A Death System Post COVID - With Special Guest Dr. Clayton Baker🔥🔥
456 watching -
 DVR
DVR
Bannons War Room
2 months agoWarRoom Live
14.5M3.95K -
 LIVE
LIVE
The Mel K Show
1 hour agoMORNINGS WITH MEL K - 4/29/25 Canada Chooses Globalism, Lack of Accountability is Allowing Chaos, Americans Wide Awake
635 watching -

BitLab Academy
1 hour agoEthereum Mega Pump Loading? Bitcoin Price Targets | Altcoin Super cycle?
8.47K -
 LIVE
LIVE
LFA TV
15 hours agoALL DAY LIVE STREAM - TUESDAY 4/29/25
3,096 watching -
 1:22:38
1:22:38
The Big Mig™
4 hours agoWho The Fook Is That Guy? Another Nobody Going After Trump!
8.49K7 -
 1:00:49
1:00:49
VINCE
3 hours agoJB Pritzker Has Big, Fat Presidential Ambitions | Episode 32 - 04/29/25
152K228